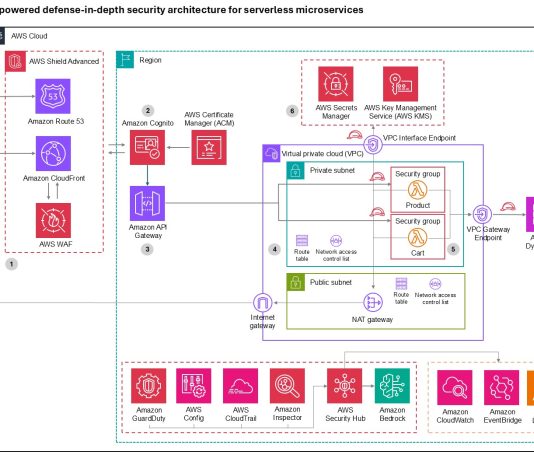
Centrify Zero Trust Security Partners in the Spotlight at RSA Booth 501
RSA Conference has moved back to April this year, and next week the largest cybersecurity trade show in the world will once again convene...
Netskope
<img src="/sites/default/files/NET_horizontal_fullcolor.png">
DG and Netskope for enterprise DLP + cloud access security
- Read more
Smart Cloud Security
Learn More
DG and Netskope for enterprise DLP + cloud access security
1
- Read more
Stop Breaches with Analytics and Artificial Intelligence
According to Gartner, companies will spend up to $96 billion worldwide on security this year, but research by Centrify and Dow Jones suggests that...
Why the Path Towards Zero Trust Starts with Next-Gen Access
Zero Trust Security has gained a lot of popularity over the last six months. Almost daily you can read articles about this security strategy...
Pocket cryptofarms
In recent months, the topic of cryptocurrency has been a permanent news fixture — the value of digital money has been see-sawing spectacularly. Such...
GDPR and Privacy: How to Earn the Trust of Your Customers and Keep Regulators...
Customer data is the lifeblood of any organisation and the key to unlocking sales and growth. But the data you hold and how you...
Your new friend, KLara
While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data...
Real-Life Exposed Privileged Identity Theft
Have you ever had your identity stolen? Credit cards obtained under your name that were not yours?
Most of us have, and what a pain...