World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my...
Who’s who in the Zoo
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation...
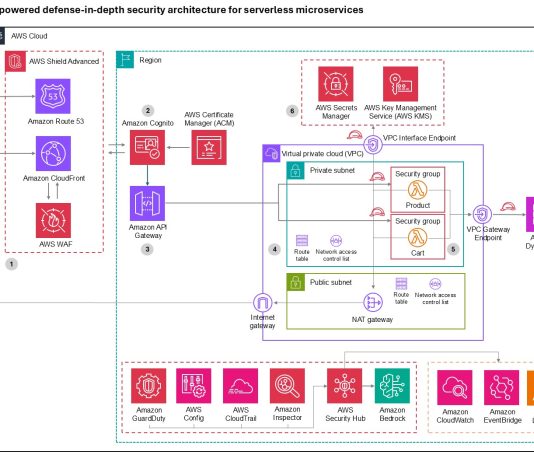
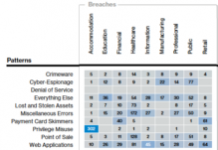
Insights from the Verizon 2018 Data Breach Investigation Report
The 2018 Verizon Data Breach Investigation Report (DBIR) was published in early April, reporting on 53,308 security incidents and 2,216 data breaches from 67...
DevSecOps Gathers More of the Spotlight at RSA 2018
Nearly 1,200 security professionals recently attended the DevOps Connect: DevSecOps Day at the 2018 RSA Conference at San Francisco’s Moscone Center.
Now in its fourth...
FS-ISAC 2018 Summit
<img src="https://info.digitalguardian.com/rs/768-OQW-145/images/fsi-isac-logo.png">
Digital Guardian will be presenting and exhibiting in Booth #69.Get tools, tips and recipes from our threat hunting experts.
Boca Raton |...
Analyst Insights – The 4 Questions for GDPR Success
Bloor Research
Analyst Insights – The 4 Questions for GDPR Success
This webinar was recorded April 26, 2018.
- Read more
DDoS attacks in Q1 2018
News overview
In early January, it was reported that an amateur hacker had come close to pulling off a botnet attack using “improvised” materials. Armed...
Supply Chain Risk: Time to Focus on Partners Ahead of GDPR Deadline
With the GDPR compliance deadline of May 25 almost upon us, recent events have highlighted the importance of locking down third-party risk. Attacks on...