Threats posed by using RATs in ICS
While conducting audits, penetration tests and incident investigations, we have often come across legitimate remote administration tools (RAT) for PCs installed on operational technology...
Stay Secure with Day-One Support for iOS 12 and macOS Mojave
It’s that time of year again: time for all the latest and greatest from our friends in Apple Park (or the Apple Spaceship as...
New trends in the world of IoT threats
Cybercriminals’ interest in IoT devices continues to grow: in H1 2018 we picked up three times as many malware samples attacking smart devices as...
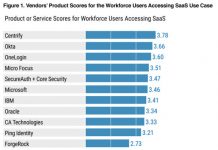
Centrify Scores Highest for Both “Workforce Users Accessing SaaS” and “Business-to-Business” in New Gartner...
Gartner just released their first ever “Critical Capabilities for Access Management, Worldwide, 2018” report, and we are proud to see that Centrify has scored...
LuckyMouse signs malicious NDISProxy driver with certificate of Chinese IT company
What happened?
Since March 2018 we have discovered several infections where a previously unknown Trojan was injected into the lsass.exe system process memory. These implants...
Threat Landscape for Industrial Automation Systems in H1 2018
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and...
We know what your kids did this summer
For many kids and teenagers, summer is all about ditching school books in favor of hobbies and fun. Every year we release a report...
What are botnets downloading?
Spam mailshots with links to malware and bots downloading other malware are just a couple of botnet deployment scenarios. The choice of infectious payload...