DoT for RPZ distribution
Read more
Start Your Engines! It’s Zero Trust Privilege Test Drive Season!
As organizations struggle to protect the ever-expanding attack surface, they not only have to secure access to infrastructure, databases, and network devices, but also...
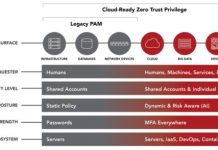
NEW CENTRIFY SURVEY: Too Much Privilege, Not Enough PAM Powered by Zero Trust
I’m both a technology guy, and a numbers guy.
I have Bachelor of Science degrees in both Accounting and Computer Science. I’ve held the CFO...
How to Attack and Defend a Prosthetic Arm
The IoT world has long since grown beyond the now-ubiquitous smartwatches, smartphones, smart coffee machines, cars capable of sending tweets and Facebook posts and...
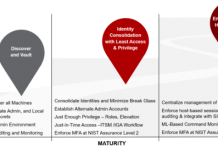
Gartner Names PAM a Top Security Project (AGAIN!) in 2019
Last June at the 2018 Gartner Security & Risk Management Summit, the analyst firm issued a “Smarter with Gartner” paper outlining the Top 10...
Threats to users of adult websites in 2018
More graphs and statistics in full PDF version
Introduction
2018 was a year that saw campaigns to decrease online pornographic content and traffic. For example, one...
ATM robber WinPot: a slot machine instead of cutlets
Automation of all kinds is there to help people with their routine work, make it faster and simpler. Although ATM fraud is a very...
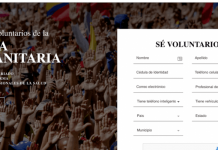
DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign
Venezuela is a country facing an uncertain moment in its history. Reports suggests it is in significant need of humanitarian aid.
On February 10th, Mr....
DDoS Attacks in Q4 2018
News overview
In Q4 2018, security researchers detected a number of new botnets, which included not only Mirai clones for a change. The fall saw...