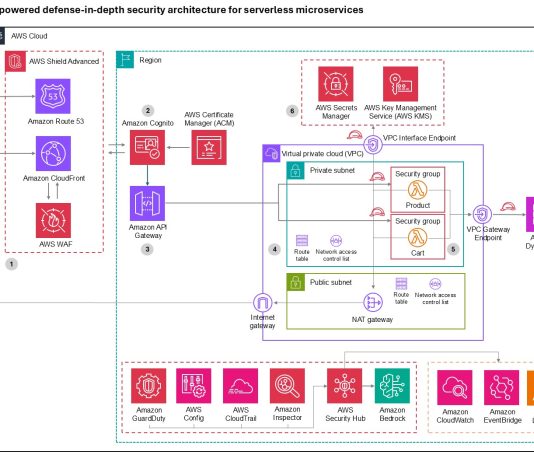
CVE-2026-21511 Microsoft Outlook Spoofing Vulnerability
Acknowledgement added. This is an informational change only. - Read more
CVE-2026-21256 GitHub Copilot and Visual Studio Remote Code Execution Vulnerability
Changes made to the security updates links and information. This is an informational change only. - Read more
Mispadu Phishing Malware Baseline: Delivery Chains, Capabilities, and Common Campaigns
By: Max Gannon, Intelligence TeamMispadu is a long-standing Banking Trojan that has only continued to grow in popularity since its first observation in 2019....
GeoServer Targeting on the Rise
Sensor Intel Series: January 2026 CVE Trends - Read more
New threat actor, UAT-9921, leverages VoidLink framework in campaigns
Cisco Talos recently discovered a new threat actor, UAT-9921, leveraging VoidLink in campaigns. Their activities may go as far back as 2019, even without...
From 27 Steps to 5: How Recorded Future Reimagined Threat Hunting with Autonomous Threat...
The manual operations gap can be a business risk Manual threat hunting requires 27 steps that burn analyst time...
Microsoft Patch Tuesday for February 2026 — Snort rules and prominent vulnerabilities
Microsoft has released its monthly security update for February 2026, which includes 59 vulnerabilities affecting a range of products, including two that Microsoft marked as “Critical”. CVE-2026-21522 is a critical elevation of privilege...
Apple Expands iPhone Driver’s Licenses to 7 US States
Apple says seven more US states plan to support iPhone driver’s licenses, expanding Apple Wallet digital IDs already live in 13 states.
The post Apple...
10K Claude Desktop Users Exposed by Zero-Click Vulnerability
A zero-click flaw in Anthropic’s Claude Desktop Extensions allows attackers to trigger remote code execution via Google Calendar events.
The post 10K Claude Desktop Users...