Learnings from recent npm supply chain compromises
A look at recent npm supply chain compromises and how we can learn from them to better prepare for future incidents. - Read...
Dell Storage Manager Multiple Vulnerabilities
Dell Storage Manager Multiple Vulnerabilities CVE-2025-43995: Authentication Bypass in DSM Data Collector (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H) An unauthenticated remote attacker can access APIs exposed by ApiProxy.war in DataCollectorEar.ear...
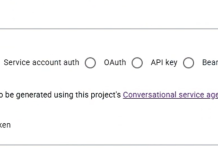
Google Cloud Platform (GCP) Dialogflow Service Agent Token Leak and Abuse Through Conversational Agents
Google Cloud Platform (GCP) Dialogflow Service Agent Token Leak and Abuse Through Conversational Agents Tenable Research has identified and responsibly disclosed a critical privilege...
CoPhish: Using Microsoft Copilot Studio as a wrapper for OAuth phishing
Copilot Studio links look benign, but they can host content to redirect users to arbitrary URLs. In this post, we document a method by...
[R1] Tenable Identity Exposure Version 3.93.4 Fixes Multiple Vulnerabilities
Tenable Identity Exposure Version 3.93.4 Fixes Multiple Vulnerabilities Arnie Cabral Fri, 10/17/2025 - 10:02
Tenable Identity Exposure leverages third-party software to help provide...
Capita fined £14m for data protection failings in 2023 cyber-attack
Hackers stole personal information of 6.6m people but outsourcing firm did not shut device targeted for 58 hoursThe outsourcing company Capita has been fined...
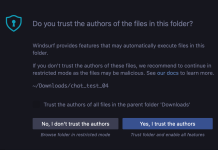
Windsurf Prompt Injection via Filename
Windsurf Prompt Injection via Filename A prompt injection vulnerability exists in Windsurf version 1.10.7. We have verified this vulnerability is present when installed on...
[R1] Security Center Version 6.7.0 Fixes One Vulnerability
Security Center Version 6.7.0 Fixes One Vulnerability Arnie Cabral Wed, 10/08/2025 - 10:29
In Tenable Security Center versions prior to 6.7.0, an improper...
Oracle E-Business Suite RCE Zero-day
Actively exploited as a zero-day in data theft and extortion campaigns, with activity linked to the Cl0p ransomware group. Successful exploitation enables complete takeover...
Fortra GoAnywhere MFT Attack
A critical deserialization vulnerability in GoAnywhere MFT’s License Servlet (CVSS 10.0) is actively being exploited in the wild. The flaw allows attackers with a...