Moving Beyond Legacy PAM: Centrify Zero Trust Privilege
Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of...
Shedding Skin – Turla’s Fresh Faces
Turla, also known as Venomous Bear, Waterbug, and Uroboros, may be best known for what was at the time an “ultra complex” snake rootkit...
Getting started with WAPIs using POSTMAN
Read more
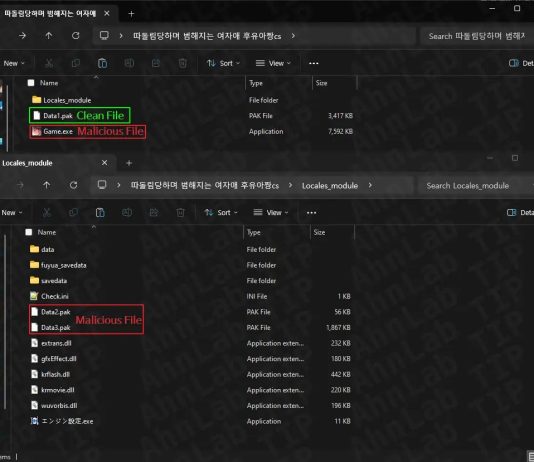
Roaming Mantis part III: iOS crypto-mining and spreading via malicious content delivery system
In Q2 2018, Kaspersky Lab published two blogposts about Roaming Mantis sharing details of this new cybercriminal campaign. In the beginning, the criminals used...
USB threats from malware to miners
Introduction
In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98%...
Threats posed by using RATs in ICS
While conducting audits, penetration tests and incident investigations, we have often come across legitimate remote administration tools (RAT) for PCs installed on operational technology...
Stay Secure with Day-One Support for iOS 12 and macOS Mojave
It’s that time of year again: time for all the latest and greatest from our friends in Apple Park (or the Apple Spaceship as...