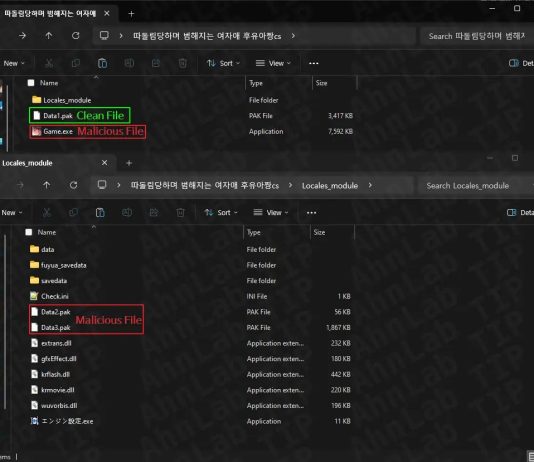
Phishing for knowledge
When we talk about phishing, top of mind are fake banking sites, payment systems, as well as mail and other globally popular services. However,...
Centrify’s new spinout, Idaptive, named Overall Leader in KuppingerCole Leadership Compass for Cloud-based MFA...
Wow! Right out of the gate and the brand new spinout of Centrify Application and Endpoint Services as Idaptive is named as an Overall...
At SecurIT in New York, it’s a Zero Trust State of Mind
On October 29-30, Centrify will proudly sponsor the second SecurIT: the Zero Trust Summit for CIOs and CISOs in New York City. Produced by...
Octopus-infested seas of Central Asia
For the last two years we have been monitoring a Russian-language cyberespionage actor that focuses on Central Asian users and diplomatic entities. We named...
Threats in the Netherlands
Introduction
On October 4, 2018, the MIVD held a press conference about an intercepted cyberattack on the OPWC in the Netherlands, allegedly by the advanced...
MuddyWater expands operations
Summary
MuddyWater is a relatively new APT that surfaced in 2017. It has focused mainly on governmental targets in Iraq and Saudi Arabia, according to...
Zero-day exploit (CVE-2018-8453) used in targeted attacks
Yesterday, Microsoft published their security bulletin, which patches CVE-2018-8453, among others. It is a vulnerability in win32k.sys discovered by Kaspersky Lab in August. We...