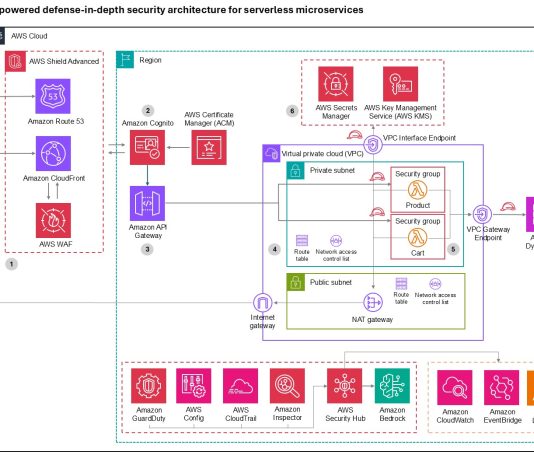
South Korea fines Louis Vuitton, Christian Dior, Tiffany $25M for SaaS security failures
South Korea’s data protection authority has handed down a combined KRW 36 billion (approximately US$25 million) in administrative fines to...
Malicious Chrome AI Extensions Attacking 260,000 Users via Injected IFrames
A coordinated campaign is using malicious Chrome extensions that impersonate popular AI tools like ChatGPT, Claude, Gemini, and Grok. These fake “AI assistants” spy...
Ransomware Groups Claimed 2,000 Attacks in Just Three Months
Ransomware attacks surged 52% in 2025, with supply chain breaches nearly doubling as groups like Qilin drive record monthly incidents worldwide.
The post Ransomware Groups...
CVE-2025-59213 Configuration Manager Elevation of Privilege Vulnerability
Updated information to include CVSS scores. This is an informational change only. - Read more
CVE-2026-21517 Windows App for Mac Installer Elevation of Privilege Vulnerability
Download links fixed - Read more
Munich Security Conference: Cyber Threats Lead G7 Risk Index, Disinformation Ranks Third
G7 countries ranked cyber-attacks as the top risk, while BICS members placed cyber threats only as the eighth most pressing risk - Read...
Fake AI Assistants in Google Chrome Web Store Steal Passwords and Spy on Emails
Hundreds of thousands of users have downloaded malicious AI extensions masquerading as ChatGPT, Gemini, Grok and others, warn cybersecurity researchers at LayerX -...
Critical Apple Flaw Exploited in ‘Sophisticated’ Attacks, Company Urges Rapid Patching
Apple urges users to update after patching CVE-2026-20700, a zero-day flaw exploited in sophisticated targeted attacks across multiple devices.
The post Critical Apple Flaw Exploited...
Hand over the keys for Shannon’s shenanigans
Welcome to this week’s edition of the Threat Source newsletter. Last week, yet another security AI tool made the rounds on social media: Shannon, a fully autonomous...
[R1] Nessus Agent Versions 11.0.4 and 11.1.2 Fix One Vulnerability
Nessus Agent Versions 11.0.4 and 11.1.2 Fix One Vulnerability Arnie Cabral Thu, 02/12/2026 - 10:40
A vulnerability has been identified where weak file...