VERT Threat Alert
Tripwire, Inc.
Watch: An Account Takeover Attack Using Credential Stuffing, and How to Protect Against It...
As cryptocurrencies continue to grow in diversity, so too do the threats they face, specifically those targeting the cryptocurrency exchange. Now, more than ever,...
Learn the essential DevOps practices that today’s most successful organizations are implementing
Learn the essential DevOps practices that today's most successful organizations are implementing ...
Spam and phishing in Q2 2018
Quarterly highlights
GDPR as a phishing opportunity
In the first quarter, we discussed spam designed to exploit GDPR (General Data Protection Regulation), which came into effect...
Enhanced Infrastructure DDoS Protection Analytics: Targeted Visibility for Greater Accuracy
We’ve rolled out enhanced infrastructure protection analytics which shows top traffic patterns for traffic flowing through our Incapsula Infrastructure DDoS Protection service.
Imperva clients can...
Implementing Modern Approaches to Database Authentication and Authorization
The most common question I hear about Database Accounts is, “Can your solution vault Database Service and other Privileged Database Accounts?”
Every time I hear...
CIS Controls and Tripwire Solutions
CIS Controls and Tripwire Solutions #outlook a{ padding:0; } body{ width:100% !important;...
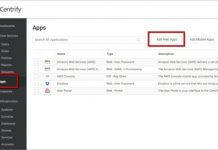
How to Authenticate Users Into Apps Using AWS Application Load Balancer and Centrify
At Centrify, an AWS Partner Network (APN) Advanced Technology Partner, we frequently work with developers building applications on Amazon Web Services (AWS). While many aspects of app...
Centrify Zero Trust Security Network Partners Highlighted at BlackHat USA 2018 Booth 2410
This week, BlackHat USA commemorates its 21st year, taking over the Mandalay Bay Convention Center in Las Vegas to present trainings as well as...
IT threat evolution Q2 2018
Targeted attacks and malware campaigns
Operation Parliament
In April, we reported the workings of Operation Parliament, a cyber-espionage campaign aimed at high-profile legislative, executive and judicial...