Microsoft and Imperva Collaboration Bolsters Data Compliance and Security Capabilities
This article explains how Imperva SecureSphere V13.2 has leveraged the latest Microsoft EventHub enhancements to help customers maintain compliance and security controls as regulated...
Integrating Security into DevOps Without Losing Momentum
Integrating Security into DevOps Without Losing Momentum #outlook a{ padding:0; } body{...
New trends in the world of IoT threats
Cybercriminals’ interest in IoT devices continues to grow: in H1 2018 we picked up three times as many malware samples attacking smart devices as...
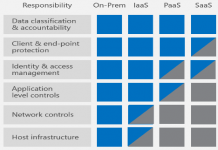
Explainer Series: RDaaS Security and Managing Compliance Through Database Audit and Monitoring Controls
As organizations move to cloud database platforms they shouldn’t forget that data security and compliance requirements remain an obligation. This article explains how you...
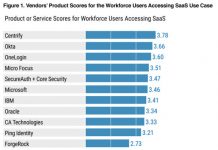
Centrify Scores Highest for Both “Workforce Users Accessing SaaS” and “Business-to-Business” in New Gartner...
Gartner just released their first ever “Critical Capabilities for Access Management, Worldwide, 2018” report, and we are proud to see that Centrify has scored...
Taking Stock: The Internet of Things, and Machine Learning Algorithms at War
It’s in the news every day; hackers targeting banks, hospitals, or, as we’ve come to fear the most, elections.
Suffice to say then that cybersecurity...
Mastering Container Security: Docker, Kubernetes and More
Mastering Container Security: Docker, Kubernetes and More #outlook a{ padding:0; } body{...
LuckyMouse signs malicious NDISProxy driver with certificate of Chinese IT company
What happened?
Since March 2018 we have discovered several infections where a previously unknown Trojan was injected into the lsass.exe system process memory. These implants...