How to Protect Your Critical Assets from Malware
How to Protect Your Critical Assets from Malware #outlook a{ padding:0; }...
Roaming Mantis part III: iOS crypto-mining and spreading via malicious content delivery system
In Q2 2018, Kaspersky Lab published two blogposts about Roaming Mantis sharing details of this new cybercriminal campaign. In the beginning, the criminals used...
The World’s Most Popular Coding Language Happens to be Most Hackers’ Weapon of Choice
Python will soon be the world’s most prevalent coding language.
That’s quite a statement, but if you look at its simplicity, flexibility and the...
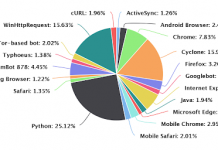
Five Insights from the Verizon 2018 DBIR
Five Insights from the Verizon 2018 DBIR #outlook a{ padding:0; } body{...
USB threats from malware to miners
Introduction
In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98%...
Imperva Joins Global Cybersecurity Tech Accord
Imperva is dedicated to the global fight to keep people’s data and applications safe from cybercriminals. What this means for our Imperva Threat Research...
Threats posed by using RATs in ICS
While conducting audits, penetration tests and incident investigations, we have often come across legitimate remote administration tools (RAT) for PCs installed on operational technology...
Stay Secure with Day-One Support for iOS 12 and macOS Mojave
It’s that time of year again: time for all the latest and greatest from our friends in Apple Park (or the Apple Spaceship as...