Octopus-infested seas of Central Asia
For the last two years we have been monitoring a Russian-language cyberespionage actor that focuses on Central Asian users and diplomatic entities. We named...
Threats in the Netherlands
Introduction
On October 4, 2018, the MIVD held a press conference about an intercepted cyberattack on the OPWC in the Netherlands, allegedly by the advanced...
MuddyWater expands operations
Summary
MuddyWater is a relatively new APT that surfaced in 2017. It has focused mainly on governmental targets in Iraq and Saudi Arabia, according to...
Zero-day exploit (CVE-2018-8453) used in targeted attacks
Yesterday, Microsoft published their security bulletin, which patches CVE-2018-8453, among others. It is a vulnerability in win32k.sys discovered by Kaspersky Lab in August. We...
Is it time to fire your vulnerability management provider?
Is it time to fire your vulnerability management provider? #outlook a{ padding:0;...
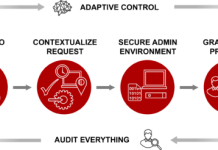
Moving Beyond Legacy PAM: Centrify Zero Trust Privilege
Our customers trust us to keep their most privileged credentials – the “keys to the kingdom” – secure from being exploited. Over half of...
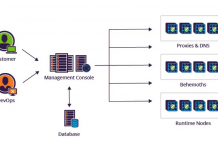
Read: How To Build Resilient Cloud Configuration Shields
Configurable systems have a high level of flexibility and are better adapted to most customer needs, but their management isn’t a trivial task in...
Shedding Skin – Turla’s Fresh Faces
Turla, also known as Venomous Bear, Waterbug, and Uroboros, may be best known for what was at the time an “ultra complex” snake rootkit...
Getting started with WAPIs using POSTMAN
Read more