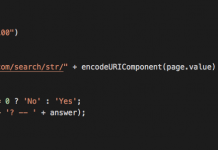
DirtyCOW Bug Drives Attackers to A Backdoor in Vulnerable Drupal Web Servers
In this post we’ll unpack a short — but no less serious — attack that affected some Linux-based systems, on October 31. Throughout the...
With The NASDAQ Bell Ceremony, We Kick Off The Next Leg of Imperva’s Incredible...
On Friday morning our CEO Chris Hylen and company execs rung the NASDAQ opening bell in New York, welcoming another day of trading for...
Imperva and Amazon Partner to Help Mitigate Risks Associated With Cloud Migration
Helping our customers reduce the risks associated with migrating to the cloud, and preventing availability and security incidents, has been a major development focus...
Black Friday alert
Banking Trojans traditionally target users of online financial services; looking for financial data to steal or building botnets out of hacked devices for future...
Forrester Names Centrify a Leader in Privileged Identity Management
Today Forrester Research released The Forrester Wave: Privileged Identity Management, Q4 20181. Evaluating 11 vendors, Forrester named Centrify a Leader.
Here at Centrify, we believe this...
A new exploit for zero-day vulnerability CVE-2018-8589
Yesterday, Microsoft published its security bulletin, which patches a vulnerability discovered by our technologies. We reported it to Microsoft on October 17, 2018. The...
Five Tips for NERC CIP Audits
Five Tips for NERC CIP Audits #outlook a{ padding:0; } body{ width:100%...
Patched Facebook Vulnerability Could Have Exposed Private Information About You and Your Friends
In a previous blog we highlighted a vulnerability in Chrome that allowed bad actors to steal Facebook users’ personal information; and, while digging around...