How to Attack and Defend a Prosthetic Arm
The IoT world has long since grown beyond the now-ubiquitous smartwatches, smartphones, smart coffee machines, cars capable of sending tweets and Facebook posts and...
Latest Drupal RCE Flaw Used by Cryptocurrency Miners and Other Attackers
Another remote code execution vulnerability has been revealed in Drupal, the popular open-source Web content management system. One exploit — still working at time...
No One is Safe: the Five Most Popular Social Engineering Attacks Against Your Company’s...
Your Wi-Fi routers and access points all have strong WPA2 passwords, unique SSIDs, the latest firmware updates, and even MAC address filtering. Good job,...
Gartner Names PAM a Top Security Project (AGAIN!) in 2019
Last June at the 2018 Gartner Security & Risk Management Summit, the analyst firm issued a “Smarter with Gartner” paper outlining the Top 10...
Threats to users of adult websites in 2018
More graphs and statistics in full PDF version
Introduction
2018 was a year that saw campaigns to decrease online pornographic content and traffic. For example, one...
How to introduce security without losing the benefits of containers
How to introduce security without losing the benefits of containers #outlook a{...
ATM robber WinPot: a slot machine instead of cutlets
Automation of all kinds is there to help people with their routine work, make it faster and simpler. Although ATM fraud is a very...
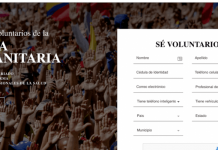
DNS Manipulation in Venezuela in regards to the Humanitarian Aid Campaign
Venezuela is a country facing an uncertain moment in its history. Reports suggests it is in significant need of humanitarian aid.
On February 10th, Mr....
How Imperva’s New Attack Crowdsourcing Secures Your Business’s Applications
Attacks on applications can be divided into two types: targeted attacks and “spray and pray” attacks. Targeted attacks require planning and usually include a...