[Case Study] Securing Your Data In The Cloud
Tripwire, Inc.
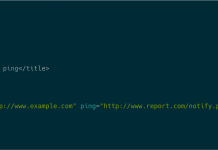
The Ping is the Thing: Popular HTML5 Feature Used to Trick Chinese Mobile Users...
DDoS attacks have always been a major threat to network infrastructure and web applications.
Attackers are always creating new ways to exploit legitimate services...
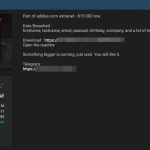
Large-scale SIM swap fraud
Introduction
SIM swap fraud is a type of account takeover fraud that generally targets a weakness in two-factor authentication and two-step verification, where the second...
Gaza Cybergang Group1, operation SneakyPastes
Gaza Cybergang(s) is a politically motivated Arabic-language cyberthreat actor, actively targeting the MENA (Middle East North Africa) region, especially the Palestinian Territories.
The confusion surrounding...
Project TajMahal – a sophisticated new APT framework
Executive summary
‘TajMahal’ is a previously unknown and technically sophisticated APT framework discovered by Kaspersky Lab in the autumn of 2018. This full-blown spying framework...
The Industrial Control System Visibility Imperative
The Industrial Control System Visibility Imperative #outlook a{ padding:0; } body{ width:100%...
Making Our Security Portfolio Simpler — and Better
Since its inception in 2009, Incapsula has been a proud part of Imperva, the analyst-recognized cybersecurity leader.
However, cybersecurity needs are evolving, and so...
BasBanke: Trend-setting Brazilian banking Trojan
BasBanke is a new Android malware family targeting Brazilian users. It is a banking Trojan built to steal financial data such as credentials and...
Roaming Mantis, part IV
One year has passed since we published the first blogpost about the Roaming Mantis campaign on securelist.com, and this February we detected new activities...
Not just for Processing: How Kafka Streams as a Distributed Database Boosted our Reliability...
The Apache Kafka Streams library is used by enterprises around the world to perform distributed stream processing on top of Apache Kafka. One aspect...


![[Case Study] Securing Your Data In The Cloud](https://www.dataproof.co.za/wp-content/uploads/2019/04/case-study-securing-your-data-in-the-cloud.jpg)