Subscriber Services
Read more
Developers Versus Automation Engineers: How We Ended the Fighting with the Right CI Process
Hey developers and DevOps professionals: what if I told you that how you wrap and execute your automation tests could be the key to...
Maintaining Privacy in the Cloud [Podcast Discussion]
Not long ago I joined Brian Contos, CISO and VP of Product Innovation at Verodin, for one of his Verodin Cybersecurity Effectiveness Podcasts.
It’s been...
Better Together: Fix Vulnerabilities Faster with FIM and VM
Better Together: Fix Vulnerabilities Faster with FIM and VM #outlook a{ padding:0;...
3 for 3! Centrify a Leader in 2019 KuppingerCole Leadership Compass for PAM
KuppingerCole recently published its 2019 KuppingerCole Leadership Compass for Privileged Access Management (PAM), again recognizing Centrify as a Leader as it did in the...
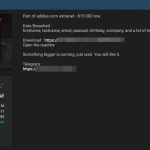
Operation ShadowHammer: a high-profile supply chain attack
In late March 2019, we briefly highlighted our research on ShadowHammer attacks, a sophisticated supply chain attack involving ASUS Live Update Utility, which was...
Gemalto shares will be delisted on 29 May 2019
- Read more
Casino Goes All In and Wins Big with Imperva Security
There’s no good time to be hit by ransom-seeking DDoS attackers. For one casino-entertainment provider, the timing was particularly bad — right before one...
How to Migrate to the Cloud Without Compromising Your Security Posture
How to Migrate to the Cloud Without Compromising Your Security Posture #outlook...
New zero-day vulnerability CVE-2019-0859 in win32k.sys
In March 2019, our automatic Exploit Prevention (EP) systems detected an attempt to exploit a vulnerability in the Microsoft Windows operating system. Further analysis...