DDoS attacks in Q1 2019
News overview
The start of the year saw the appearance of various new tools in the arsenal of DDoS-attack masterminds. In early February, for instance,...
Spam and phishing in Q1 2019
Quarterly highlights
Valentine’s Day
As per tradition, phishing timed to coincide with lovey-dovey day was aimed at swindling valuable confidential information out of starry-eyed users, such...
Cloud Security Risks and Solutions
Cloud Security Risks and Solutions #outlook a{ padding:0; } body{ width:100% !important;...
Cloud WAAPs Are the Future of Application Security. But What Does That Mean?
Millions of Verizon FIOS broadband users vulnerable to hackers controlling and surveilling their home networks.
Thousands of GPS watches whose maps were open to attackers...
ScarCruft continues to evolve, introduces Bluetooth harvester
Executive summary
After publishing our initial series of blogposts back in 2016, we have continued to track the ScarCruft threat actor. ScarCruft is a Korean-speaking...
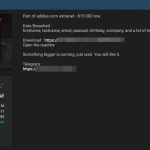
Take these Five Steps to Really Mitigate your Data Breach Risks
Data breaches are a CSO/CISO’s worst nightmare. And they’re getting bigger and more damaging all the time. It’s no longer just hundreds of millions...
The 2019 DBIR is out
Once again, we are happy to support a large, voluntary, collaborative effort like the 2019 Data Breach Investigations Report. While our data contribution is...
FIN7.5: the infamous cybercrime rig “FIN7” continues its activities
On August 1, 2018, the US Department of Justice announced that it had arrested several individuals suspected of having ties to the FIN7 cybercrime...