Gas is too expensive? Let’s make it cheap!
A few months ago, while undertaking unrelated research into online connected devices, we uncovered something surprising and realized almost immediately that we could be...
Escaping Data-Breach Groundhog Day
Countless companies globally are trapped in data breach Groundhog Day, unable to escape a repeating cycle of cyber attacks.
In the 2018 Thales Data Threat...
2017 OWASP Top 10: The Good, the Bad and the Ugly
Since its founding in 2001, the Open Web Application Security Project (OWASP) has become a leading resource for online security best practices. In particular,...
What do Equifax, HBO, Uber and Yahoo All Have in Common?
A consumer ratings agency, a cable network, a transportation company and a web services provider. What ties them together? Sure, they were all impacted...
Every little bitcoin helps
It often happens that inventions and technologies that start out good end up turning into dangerous tools in the hands of criminals. Blockchain is...
Cybercriminals target early IRS 2018 refunds now
On Monday, Jan 29th, IRS officially opened its 2018 season. Some taxpayers already filed their taxes and cybercriminals know it too. So, right after...
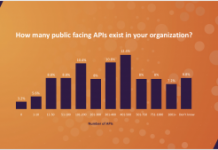
Survey: APIs a Growing Cybersecurity Risk
Like a lot of people, your mobile phone number is probably easily accessible to anyone with a bit of searching. Imagine if someone could...
Improve the ROI of Your Database Protection Investment
When an organization considers switching a mission-critical compliance or security system from one vendor’s solution to another it’s a very big decision. There is...
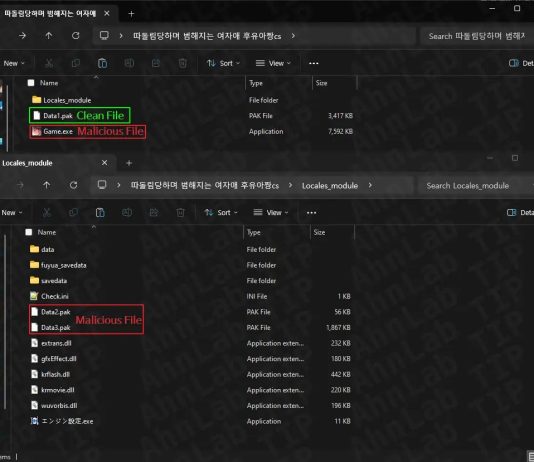
Denis and Co.
In April 2017, we published a detailed review of a malicious program that used DNS tunneling to communicate to its C&C. That study prompted...
Centrify to Discuss Zero Trust Security at the ICIT 2018 Winter Summit
Following the high-profile breach of the US Office of Personnel Management (OPM), which exposed the personal data of millions of Americans, the House of Representatives’...