A Slice of 2017 Sofacy Activity
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to...
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our...
Spam and phishing in 2017
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US...
Integrate Your Ticketing System into Database Security to Prevent DBA Privilege Abuse
Many of the recent high-profile data security breaches were made by trusted insiders. They are often database administrators (DBAs) who are highly privileged and...
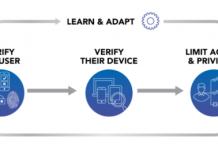
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...
A Deep Dive into Database Attacks [Part I]: SQL Obfuscation
Today, data breaches are a threat to every organization. According to a report from Risk Based Security covering the first half of 2017, over 6...
RSA 2018
RSA 2018
Digital Guardian will be exhibiting at RSA 2018. Discover all the things happening at our booth and beyond!
...
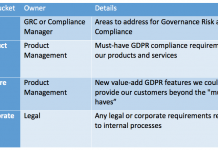
One GRC Manager’s Practical Approach to GDPR Readiness
With about four months to go before the GDPR becomes effective many companies are still struggling with where to start. You’re not alone. According...
A vulnerable driver: lesson almost learned
Recently, we started receiving suspicious events from our internal sandbox Exploit Checker plugin. Our heuristics for supervisor mode code execution in the user address...
Zero Trust Security for the New Australian Data Breach Law
Many Australian businesses need to rethink their approach to security to prepare for their nation’s new mandatory data breach notification law which take effect...






![A Deep Dive into Database Attacks [Part I]: SQL Obfuscation](https://www.dataproof.co.za/wp-content/uploads/2018/02/a-deep-dive-into-database-attacks-part-i-sql-obfuscation-218x150.png)