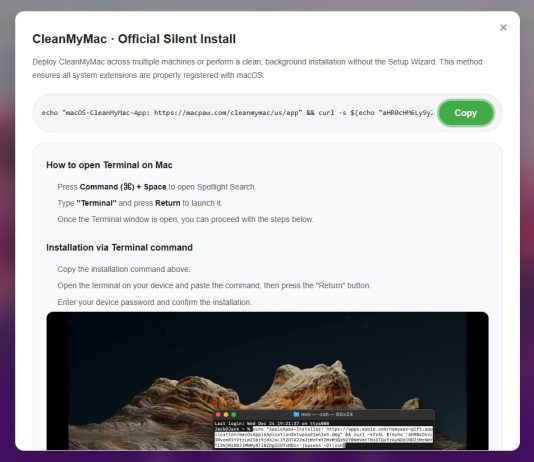
Metasploit 2025 Annual Wrap-Up
Hard to believe it's that time again, and that Metasploit Framework will see the dawn of another Annual Wrap-Up (and a New Year). All...
5th January – Threat Intelligence Report
For the latest discoveries in cyber research for the week of 5th January, please download our Threat Intelligence Bulletin.
TOP ATTACKS AND BREACHES
Two US banks,...
New ransomware tactics to watch out for in 2026
Key Takeaways Declining payments, evolving tactics: Ransomware groups made less money in 2025 despite a 47% increase in publicly reported attacks, pushing...
29th December – Threat Intelligence Report
For the latest discoveries in cyber research for the week of 29th December, please download our Threat Intelligence Bulletin.
TOP ATTACKS AND BREACHES
Romanian Waters, the...
The HoneyMyte APT evolves with a kernel-mode rootkit and a ToneShell backdoor
Overview of the attacks
In mid-2025, we identified a malicious driver file on computer systems in Asia. The driver file is signed with an old,...
A Note from our Executive Director
This letter was originally published in our 2025 Annual Report.
This year was the 10th anniversary of Let’s Encrypt. We’ve come a long way!...
WIRED – 2,364,431 breached accounts
In December 2025, 2.3M records of WIRED magazine users allegedly obtained from parent company Condé Nast were published online. The most recent data dated...
‘All brakes are off’: Russia’s attempt to rein in illicit market for leaked data...
Russian state has tolerated parallel probiv market for its convenience but now Ukrainian spies are exploiting itRussia is scrambling to rein in the country’s...