Making Headlines: SAML
On February 27, 2018 the CERT Division of Carnegie Mellon University’s Software Engineering Institute issued advisory #475445, outlining a design flaw in Security Assertion...
Goodfellas, the Brazilian carding scene is after you
There are three ways of doing things in the malware business: the right way, the wrong way and the way Brazilians do it. From...
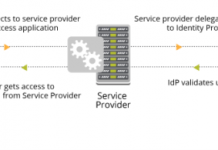
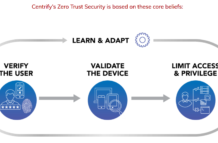
Centrify for NIST 800-171 MFA Compliance
I often speak with Federal System Integrators (FSIs) who need to implement Multi-Factor Authentication (MFA) as part of their NIST 800-171 compliance.
Specifically section 3.5.3...
OT Cybersecurity – Securing Your Industrial Operations for Reliability and Uptime
OT Cybersecurity - Securing Your Industrial Operations for Reliability and Uptime #outlook...
A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My...
As part of Imperva’s efforts to protect our customers’ data, we have an ongoing research project focused on analyzing and sharing different attack methods...
Time of death? A therapeutic postmortem of connected medicine
#TheSAS2017 presentation: Smart Medicine Breaches Its “First Do No Harm” Principle
At last year’s Security Analyst Summit 2017 we predicted that medical networks would be...
SEC Clarification: Companies Must Disclose Breaches
In late February, the U.S. Security and Exchange Commission (SEC) issued new cybersecurity guidance in the form of an “interpretive release.” According to the...
Somebody’s watching! When cameras are more than just ‘smart’
Every year the number of smart devices grows. Coffee machines, bracelets, fridges, cars and loads of other useful gadgets have now gone smart. We...
Masha and these Bears
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a prolific, well resourced, and persistent adversary. They are sometimes portrayed as wild...



![[Part 4/4] Practical Advice to Network and Security Operations Pros Regarding GDPR Compliance](https://www.dataproof.co.za/wp-content/uploads/2018/04/part-4-4-practical-advice-to-network-and-security-operations-pros-regarding-gdpr-compliance-218x150.jpg)

![A Deep Dive into Database Attacks [Part III]: Why Scarlett Johansson’s Picture Got My Postgre Database to Start Mining Monero](https://www.dataproof.co.za/wp-content/uploads/2018/03/a-deep-dive-into-database-attacks-part-iii-why-scarlett-johanssons-picture-got-my-postgre-database-to-start-mining-monero-218x150.png)









