Analyst Insights – The 4 Questions for GDPR Success
Bloor Research
Analyst Insights – The 4 Questions for GDPR Success
This webinar was recorded April 26, 2018.
- Read more
DDoS attacks in Q1 2018
News overview
In early January, it was reported that an amateur hacker had come close to pulling off a botnet attack using “improvised” materials. Armed...
Supply Chain Risk: Time to Focus on Partners Ahead of GDPR Deadline
With the GDPR compliance deadline of May 25 almost upon us, recent events have highlighted the importance of locking down third-party risk. Attacks on...
Five Critical Steps of a Complete Security Risk and Compliance Lifecycle
Five Critical Steps of a Complete Security Risk and Compliance Lifecycle #outlook...
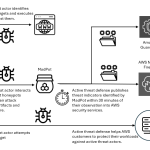
Energetic Bear/Crouching Yeti: attacks on servers
Energetic Bear/Crouching Yeti is a widely known APT group active since at least 2010. The group tends to attack different companies with a strong...
FW: Best Practices for DevOps Security
Tripwire, Inc.
FW: [Report] The Most Efficient Way to Reduce Security Risks
Tripwire, Inc.
Tens of thousands per Gram
Looking at Instagram one morning, I spotted several posts from some fairly well-known people (in certain circles) who had invested in an ICO held...
Leaking ads
When we use popular apps with good ratings from official app stores we assume they are safe. This is partially true – usually these...









![FW: [Report] The Most Efficient Way to Reduce Security Risks](https://www.dataproof.co.za/wp-content/uploads/2018/04/fw-report-the-most-efficient-way-to-reduce-security-risks.jpg)