Making Smarter Access Control Decisions
Hey Siri, block that attacker, please
Wouldn’t it be great if Siri, Alexa, or Google Assistant had the intelligence to figure out malicious intent, govern...
Pbot: evolving adware
The adware PBot (PythonBot) got its name because its core modules are written in Python. It was more than a year ago that we...
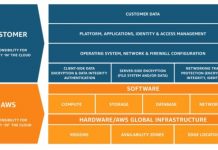
Zero Trust Security and DevOps Take the Crown at AWS Public Sector Summit 2018
Last week, Amazon Web Services hosted its AWS Public Sector Summit in Washington, DC. In its 9th year, the event attracted thousands of global...
How To Leverage Data Access Analytics for Effective Breach Detection
Detecting and preventing data breaches is a challenge for most, if not all, enterprises. In fact, according to a study released in 2017, 78%...
What’s the Financial Impact of Your VM Solution?
Tripwire, Inc.
What is Your Cyber Breach Response Strategy?
Tripwire, Inc.
Cyber Risk Insights from the AIG 2017 Cyber Insurance Review
I read with interest AIG’s 2017 Cyber Insurance Review. In a one sentence summary: cyber insurance claims are up, due to systemic ransomware and...
The Gartner CISO Playbook: Leveraging Effective Control in the Cloud
For as long as we can remember, the concept of control has rested comfortably in physical location and ownership. It’s simple, if you could...
Centrify Named a Visionary in the 2018 Magic Quadrant for Access Management, Worldwide
Download the 2018 Gartner Magic Quadrant for Access Management
Centrify has been named a Visionary by Gartner, Inc. in the 2018 Magic Quadrant for Access...