Another Ransomware Variant Strikes Colorado DOT Days after Initial Attack
Posts from The State of Security for 03/02/2018
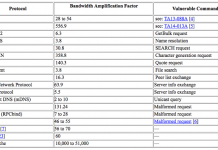
Inside a New DDoS Amplification Attack Vector via Memcached Servers
We recently saw a new DDoS amplification attack vector via memcached servers that culminated in two massive DDoS amplification attacks on February 28. Both...
Takeaways from the Russia-Linked US Senate Phishing Attacks
The Zero Trust Security approach could empower organizations and protect their customers in ways that go far beyond typical security concerns.
On January 12, 2018,...
Financial Cyberthreats in 2017
In 2017, we saw a number of changes to the world of financial threats and new actors emerging. As we have previously noted, fraud...
IoT hack: how to break a smart home… again
There can never be too many IoT gadgets – that’s what people usually think when buying yet another connected device with advanced functionality. From...
Multi-factor Authentication (MFA) Is Ready for Prime Time
We’ve heard it time and again. As security threats increase and morph, and user devices and locations diversify, multi-factor authentication (MFA) should be blossoming...
Subscribe to Data Insider
Subscribe to <span style="color: #11111; font-style: bold; letter-spacing: -1px;">DATA</span><span style="color: #E51892; font-style: italic; font-style: bold; letter-spacing: -1px;">INSIDER</span>
.blog_subscribe_block{ margin-top: 50px !important; margin-left: auto;...
NEW: Vulnerability and Assessment Scanning for Your AWS Cloud Databases
Scuba is a free and easy-to-use tool that uncovers hidden security risks. Scuba is frequently updated with content from Imperva’s Defense Center researchers.
With Scuba...
Tax refund, or How to lose your remaining cash
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...