The Slingshot APT FAQ
While analysing an incident which involved a suspected keylogger, we identified a malicious library able to interact with a virtual file system, which is...
Complete Guide to Creating a Sound IT Environment
Tripwire, Inc.
RedisWannaMine Unveiled: New Cryptojacking Attack Powered by Redis and NSA Exploits
Recently cryptojacking attacks have been spreading like wildfire. At Imperva we have witnessed it firsthand and even concluded that these attacks hold roughly 90%...
The devil’s in the Rich header
In our previous blog, we detailed our findings on the attack against the Pyeongchang 2018 Winter Olympics. For this investigation, our analysts were provided...
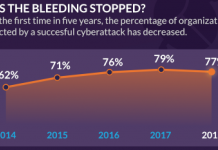
2018 Cyberthreat Defense Report: Where IT Security Is Going
What keeps you awake at night? We asked IT security professionals the same question and found that these issues are top of mind: malware...
Frost & Sullivan Recognizes Centrify for IDaaS and PIM Leadership
Today Frost & Sullivan, a leading analyst firm and growth partnership company, announced that Centrify has earned the North American Product Leadership Award for...
Protecting Your Organization from the Next Big Ransomware Threat
Protecting Your Organization from the Next Big Ransomware Threat #outlook a{ padding:0;...
Welcome to The State of Security
Welcome to The State of Security #outlook a{ padding:0; } body{ width:100%...
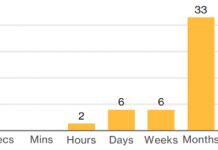
Hunting for Insider Threats: Using Activity Modeling to Detect Suspicious Database Commands and Access...
The Widening Gap
Data breaches by insiders are very challenging to catch. The gap between the rise of insider threats and speed of hunting them...
With Less Than 100 Days to Go, How to Get C-Level Buy-in for GDPR...
For GDPR compliance initiatives to work effectively, there has to be buy-in from the boardroom. That doesn’t just mean releasing the necessary funds to...