Making the Grade: Achieve SSL Labs A+ Grade with Imperva WAF
We all woke up to a new reality early last year. HTTPS adoption has reached the tipping point, meaning that more than half of...
Your new friend, KLara
While doing threat research, teams need a lot of tools and systems to aid their hunting efforts – from systems storing Passive DNS data...
18 Expert Tips for Effective and Secure Cloud Migration
18 Expert Tips for Effective and Secure Cloud Migration #outlook a{ padding:0;...
Real-Life Exposed Privileged Identity Theft
Have you ever had your identity stolen? Credit cards obtained under your name that were not yours?
Most of us have, and what a pain...
Threat Landscape for Industrial Automation Systems in H2 2017
For many years, Kaspersky Lab experts have been uncovering and researching cyberthreats that target a variety of information systems – those of commercial and...
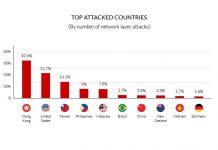
Q4 2017 Global DDoS Threat Landscape Report
Today we are releasing our latest Global DDoS Threat Landscape Report, a statistical analysis of 5,055 network and application layer DDoS attacks mitigated by...
Six Reasons to Experience Zero Trust Security in Centrify Booth 501 at RSA
In case you hadn’t heard, the 2018 RSA Conference will be held April 16-19 at the Moscone Center in San Francisco. If you haven’t...
Closing the Integrity Gap with NIST’s Cybersecurity Framework
Closing the Integrity Gap with NIST's Cybersecurity Framework #outlook a{ padding:0; }...
Data Security Solutions for GDPR Compliance
Enforcement of the new EU General Data Protection Regulation (GDPR) adopted in 2016 starts on May 25, 2018. It requires all organizations that do...