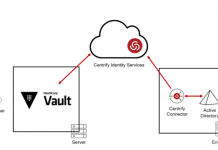
Introducing Centrify Identity Services for HashiCorp Vault
Today, Centrify is proud to announce the integration of the Centrify Identity Service with HashiCorp Vault for role-based user authentication and access to the...
Secure the Vote with Zero Trust
Our democracy is under attack.
We are in an era where digital assets are being weaponized and used against us. The fragile state of our...
It’s the Control Plane, Stupid.
Read more
Drupalgeddon 2.0: Are Hackers Slacking Off?
Ever since March 28th, when Drupal published a patch for a RCE named Drupalgeddon 2.0 (SA-CORE-2018-002/CVE-2018-7600), Imperva has been monitoring our cloud looking for...
Securing Modern Web Applications: Threats and Types of Attacks
Web Application Firewalls are the most advanced firewall capabilities available to IT teams. Deploying the appropriate WAF is important, especially these days when the...
Trends to look for next week at RSA Conference 2018
Next week (April 16-19) is the 2018 RSA Conference at the Moscone Center in San Francisco, and there’s good news: it’s not too late...
APT Trends report Q1 2018
In the second quarter of 2017, Kaspersky’s Global Research and Analysis Team (GReAT) began publishing summaries of the quarter’s private threat intelligence reports in...
Centrify Zero Trust Security Partners in the Spotlight at RSA Booth 501
RSA Conference has moved back to April this year, and next week the largest cybersecurity trade show in the world will once again convene...
Driving DevOps Security: Scalable Best Practices
Driving DevOps Security: Scalable Best Practices #outlook a{ padding:0; } body{ width:100%...
How to Tune Your Database Security to Protect Big Data
As digital information and data continues to accumulate worldwide, new big data solutions grow more and more popular. The introduction of IoT into our...