Insights from the Verizon 2018 Data Breach Investigation Report
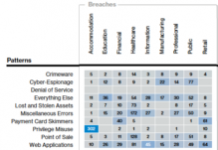
The 2018 Verizon Data Breach Investigation Report (DBIR) was published in early April, reporting on 53,308 security incidents and 2,216 data breaches from 67...
Securing the Entire Container Stack, Lifecycle and Pipeline
Securing the Entire Container Stack, Lifecycle and Pipeline #outlook a{ padding:0; }...
DevSecOps Gathers More of the Spotlight at RSA 2018
Nearly 1,200 security professionals recently attended the DevOps Connect: DevSecOps Day at the 2018 RSA Conference at San Francisco’s Moscone Center.
Now in its fourth...
The Catch 22 of Base64: Attacker Dilemma from a Defender Point of View
Web application threats come in different shapes and sizes. These threats mostly stem from web application vulnerabilities, published daily by the vendors themselves or...
[Case Study] Delivering Security Needs On Time
Tripwire, Inc.
Drupalgeddon3: Third Critical Flaw Discovered
For the third time in the last 30 days, Drupal site owners are forced to patch their installations. As the Drupal team noted a...
FS-ISAC 2018 Summit
<img src="https://info.digitalguardian.com/rs/768-OQW-145/images/fsi-isac-logo.png">
Digital Guardian will be presenting and exhibiting in Booth #69.Get tools, tips and recipes from our threat hunting experts.
Boca Raton |...
Analyst Insights – The 4 Questions for GDPR Success
Bloor Research
Analyst Insights – The 4 Questions for GDPR Success
This webinar was recorded April 26, 2018.
- Read more
DDoS attacks in Q1 2018
News overview
In early January, it was reported that an amateur hacker had come close to pulling off a botnet attack using “improvised” materials. Armed...





![[Case Study] Delivering Security Needs On Time](https://www.dataproof.co.za/wp-content/uploads/2018/04/case-study-delivering-security-needs-on-time.jpg)







