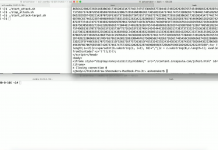
OPC UA security analysis
This paper discusses our project that involved searching for vulnerabilities in implementations of the OPC UA protocol. In publishing this material, we hope to...
Want to See What A Live DDoS Attack Looks Like?
We’re fortunate enough to have had Andy Shoemaker, founder of NimbusDDoS, and our own Ofer Gayer chat about DDoS attacks and shed some light on...
Jumpstarting Your Cyberdefense Machine with CIS Controls V7
Jumpstarting Your Cyberdefense Machine with CIS Controls V7 #outlook a{ padding:0; }...
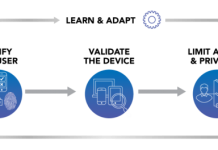
How to Operationalize the Zero Trust Security Pillar ‘Limit Access & Privilege’ with ServiceNow
An easy way for a cyber-attacker to gain access to sensitive data is by compromising an end user’s identity and credentials. Things get even...
Gartner Security & Risk Management Summit 2018
Gartner Security & Risk Management Summit 2018
June 4th – 7th | National Harbor, MD
- Read more
SynAck targeted ransomware uses the Doppelgänging technique
The Process Doppelgänging technique was first presented in December 2017 at the BlackHat conference. Since the presentation several threat actors have started using this...
World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my...
Who’s who in the Zoo
ZooPark is a cyberespionage operation that has been focusing on Middle Eastern targets since at least June 2015. The threat actors behind the operation...
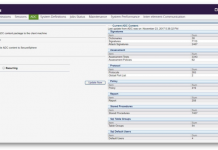
Configuring Imperva SecureSphere for GDPR Compliance: Part One
Time is running out. 23 days until GDPR enforcement
The GDPR effective date is less than a month away and, given the significant risk and...