Facebook, GDPR and the Right to Privacy: Three’s a Crowd?
Back in 2016 the European Union voted to pass the mother of all security laws, aimed at further extending the rights of its citizens...
Roaming Mantis dabbles in mining and phishing multilingually
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which...
Analyst Insights – Building An Efficient Data Security Program with Forrester
Analyst Insights – Building An Efficient Data Security Program
This webinar was recorded on May 17, 2018.
- Read more
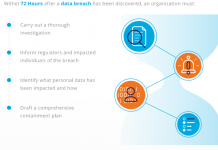
72 Hours: Understanding the GDPR Data Breach Reporting Timeline
We’re down to the wire with respect to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018.
Organizations that fail to comply...
Electronic Health Record Systems Under Attack
Electronic Health Record Systems Under Attack #outlook a{ padding:0; } body{ width:100%...
Centrify and SailPoint Join Forces to Apply Zero Trust Security Best Practices to Identity...
Today, Centrify is proud to announce the integration of the Centrify Privileged Access Service with SailPoint® Technologies IdentityIQ solution.
This integration provides joint customers with...
IT threat evolution Q1 2018. Statistics
Q1 figures
According to KSN:
Kaspersky Lab solutions blocked 796,806,112 attacks launched from online resources located in 194 countries across the globe.
282,807,433 unique URLs were...
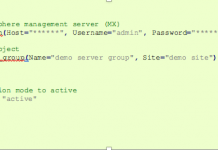
Imperva Python SDK – We’re All Consenting SecOps Here
Managing your WAF can be a complicated task. Custom policies, signatures, application profiles, gateway plugins… there’s a good reason ours is considered the best...




![[VitalQIP Migration Series] Part 1: Three Reasons Why VitalQIP Migration Should Be on Your Radar](https://www.dataproof.co.za/wp-content/uploads/2018/05/vitalqip-migration-series-part-1-three-reasons-why-vitalqip-migration-should-be-on-your-radar-218x150.jpg)