Five Ways Imperva Attack Analytics Helps You Cut Through the Event Noise
The maddening volume of events security teams have to deal with each day is growing at an exponential pace, making it increasingly difficult to effectively...
Trojan watch
We continue to research how proliferation of IoT devices affects the daily lives of users and their information security. In our previous study, we...
See If You’re GDPR-Ready With Our Last-Minute Checklist
Time’s just about run out to get all your ducks in a row for the EU’s General Data Protection Regulation (GDPR) going into effect...
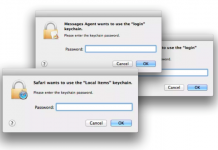
Sync Your Jaws Into Mac Keychain
“Well this is not a boat accident! It wasn’t any propeller! It wasn’t any coral reef! And it wasn’t Jack the Ripper! It was...
VPNFilter EXIF to C2 mechanism analysed
On May 23 2018, our colleagues from Cisco Talos published their excellent analysis of VPNFilter, an IoT / router malware which exhibits some worrying...
It’s Almost GDPR D-Day: So What Happens Next?
Over the past 12 months during this blog series I’ve tried to provide insight into some of the key aspects of the GDPR and...
Backdoors in D-Link’s backyard
“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want...
Threat Prevention is Foundational
Threat Prevention is Foundational #outlook a{ padding:0; } body{ width:100% !important; }...
Centrify Does it Again – Innovative Security Analytics Integration with Palo Alto Networks App...
Centrify and Palo Alto Networks have announced another important integration that can help customers quickly and decisively discover anomalies that are a security threat.
Building...