World Password Day – 5 Facts About Weak Credentials
Happy World Password Day!
Ok, I’ll admit until a few days ago, I wasn’t aware this was a thing. As with most events in my...
Insights from the Verizon 2018 Data Breach Investigation Report
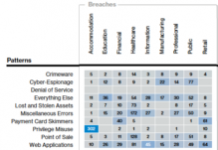
The 2018 Verizon Data Breach Investigation Report (DBIR) was published in early April, reporting on 53,308 security incidents and 2,216 data breaches from 67...
DevSecOps Gathers More of the Spotlight at RSA 2018
Nearly 1,200 security professionals recently attended the DevOps Connect: DevSecOps Day at the 2018 RSA Conference at San Francisco’s Moscone Center.
Now in its fourth...
Supply Chain Risk: Time to Focus on Partners Ahead of GDPR Deadline
With the GDPR compliance deadline of May 25 almost upon us, recent events have highlighted the importance of locking down third-party risk. Attacks on...
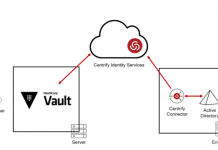
Introducing Centrify Identity Services for HashiCorp Vault
Today, Centrify is proud to announce the integration of the Centrify Identity Service with HashiCorp Vault for role-based user authentication and access to the...
Secure the Vote with Zero Trust
Our democracy is under attack.
We are in an era where digital assets are being weaponized and used against us. The fragile state of our...
Trends to look for next week at RSA Conference 2018
Next week (April 16-19) is the 2018 RSA Conference at the Moscone Center in San Francisco, and there’s good news: it’s not too late...
Centrify Zero Trust Security Partners in the Spotlight at RSA Booth 501
RSA Conference has moved back to April this year, and next week the largest cybersecurity trade show in the world will once again convene...
Stop Breaches with Analytics and Artificial Intelligence
According to Gartner, companies will spend up to $96 billion worldwide on security this year, but research by Centrify and Dow Jones suggests that...
Why the Path Towards Zero Trust Starts with Next-Gen Access
Zero Trust Security has gained a lot of popularity over the last six months. Almost daily you can read articles about this security strategy...