Centrify Launches Zero Trust Security Network Ecosystem
The world has changed. I’m not sure if it was the HBO breach, Equifax, Yahoo, or one of the many breaches since, but after...
Five Reasons to Kill Off the Password
Australia recognised the security problem posed by passwords through widespread media coverage of Centrify’s warning issued on World Password Day, which occurred on May...
451 Research: Centrify Goes “All In” on the Zero Trust Movement
451 Research recently published an impact report recognizing Centrify as one of the early vendors to embrace the Zero Trust concept, which is a...
SecurIT: Making Zero Trust a Reality for CIOs and CISOs
On June 13, C-level and senior management leaders from global companies spanning multiple industries will gather in San Francisco at SecurIT: the Zero Trust...
What’s in it for Consumers? The Top 5 Privacy Benefits of the GDPR
The General Data Protection Regulation, or GDPR for short, is a major new European privacy law that went into effect on May 25. GDPR...
Sync Your Jaws Into Mac Keychain
“Well this is not a boat accident! It wasn’t any propeller! It wasn’t any coral reef! And it wasn’t Jack the Ripper! It was...
It’s Almost GDPR D-Day: So What Happens Next?
Over the past 12 months during this blog series I’ve tried to provide insight into some of the key aspects of the GDPR and...
Centrify Does it Again – Innovative Security Analytics Integration with Palo Alto Networks App...
Centrify and Palo Alto Networks have announced another important integration that can help customers quickly and decisively discover anomalies that are a security threat.
Building...
Centrify and SailPoint Join Forces to Apply Zero Trust Security Best Practices to Identity...
Today, Centrify is proud to announce the integration of the Centrify Privileged Access Service with SailPoint® Technologies IdentityIQ solution.
This integration provides joint customers with...
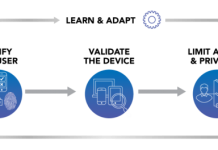
How to Operationalize the Zero Trust Security Pillar ‘Limit Access & Privilege’ with ServiceNow
An easy way for a cyber-attacker to gain access to sensitive data is by compromising an end user’s identity and credentials. Things get even...