What do Equifax, HBO, Uber and Yahoo All Have in Common?
A consumer ratings agency, a cable network, a transportation company and a web services provider. What ties them together? Sure, they were all impacted by very high-profile security breaches. But, if you dig a little deeper, you’ll find these organizations had a lot in common before, during and after their respective breaches. And those commonalities can teach us valuable...
Every little bitcoin helps
It often happens that inventions and technologies that start out good end up turning into dangerous tools in the hands of criminals. Blockchain is no exception to this rule, especially in its most common cryptocurrency incarnation. Cryptocurrencies crop up in all kinds of spam: from traditional advertising (courses about investment and trade) to more fraudulent and malicious varieties. Quite...
Cybercriminals target early IRS 2018 refunds now
On Monday, Jan 29th, IRS officially opened its 2018 season. Some taxpayers already filed their taxes and cybercriminals know it too. So, right after two days of the official 2018 season opening, we got phishing messages with a fake refund status Websites:
The link in the email leads to a hacked Brazilian restaurant, redirecting to Website with Australian domain...
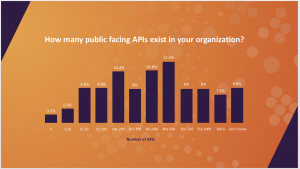
Survey: APIs a Growing Cybersecurity Risk
Like a lot of people, your mobile phone number is probably easily accessible to anyone with a bit of searching. Imagine if someone could take this number and your name and gain access to your mobile phone account including billing, email address and phone IMSI. Or maybe someone hacked into one of your social accounts and accessed your contact...
Improve the ROI of Your Database Protection Investment
When an organization considers switching a mission-critical compliance or security system from one vendor’s solution to another it’s a very big decision. There is expense involved in acquiring the new solution, it will take time and money to deploy and retrain staff, and it will take careful planning to avoid disruption in the transition.
Yet again and again, customers of...
Denis and Co.
In April 2017, we published a detailed review of a malicious program that used DNS tunneling to communicate to its C&C. That study prompted us to develop a technology to detect similar threats, which allowed us to collect a multitude of malware samples using DNS tunneling.
In this article, we will examine some of the most notable malicious programs that...
Centrify to Discuss Zero Trust Security at the ICIT 2018 Winter Summit
Following the high-profile breach of the US Office of Personnel Management (OPM), which exposed the personal data of millions of Americans, the House of Representatives’ Committee on Oversight and Government Reform issued a report on the attack in 2016.
That report provided an exhaustive account of the events leading up to the breach, illustrating how a hacker posing as an employee...
4 Months to Go: A New Year GDPR Checklist
As we enter the New Year, IT and security leaders have most likely been glued to revelations of major new CPU-level vulnerabilities Meltdown and Spectre, described by researchers as among the “worst ever” discovered. However, there’s arguably an even more pressing concern, not just for IT but the entire organisation: GDPR compliance. There are now just over four months...
Data Breaches Plague Organizations for Years
Once an organization’s network is breached, extinguishing the flames is just the first step in a long, painful and costly journey to recovery. There’s still the wreckage to sift through, investigators to perform analyses, insurance claims and, of course, a business to reconstruct and secure. It isn’t business as usual once operations are restored; a breach can plague an...
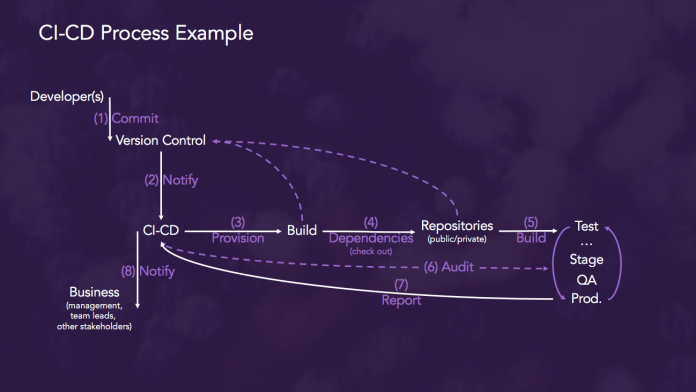
Security Strategies for DevOps, APIs, Containers and Microservices
More and more IT professionals see DevSecOps, a practice which integrates security measures earlier in the development process to improve production code quality, as a mainstay for future application development.
Much of this stems from the growing trend towards speeding up application development through adopting architectures using DevOps, containers and microservices, as well as supporting automation toolchains and frameworks. This...