VPNFilter EXIF to C2 mechanism analysed
On May 23 2018, our colleagues from Cisco Talos published their excellent analysis of VPNFilter, an IoT / router malware which exhibits some worrying characteristics.
Some of the things which stand out about VPNFilter are:
It has a redundant, multi-stage command and control mechanism which uses three different channels to receive information
It has a multi-stage architecture, in which some of...
It’s Almost GDPR D-Day: So What Happens Next?
Over the past 12 months during this blog series I’ve tried to provide insight into some of the key aspects of the GDPR and how organisations can better prepare for the big compliance deadline day of 25 May.
Now that day is almost upon us, the question many organisations are asking is, “what happens next?”
The truth is that, despite having...
Backdoors in D-Link’s backyard
“If you want to change the world, start with yourself.” In the case of security research this can be rephrased to: “If you want to make the world safer, start with the smart things in your home.” Or, to be more specific, start with your router – the core of any home network as well as an interesting research...
Threat Prevention is Foundational
Threat Prevention is Foundational #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff; }...
Centrify Does it Again – Innovative Security Analytics Integration with Palo Alto Networks App Framework
Centrify and Palo Alto Networks have announced another important integration that can help customers quickly and decisively discover anomalies that are a security threat.
Building on our past partnership, both companies collaborated anew around the Centrify Analytics Service and the Palo Alto Networks App Framework to more-readily share threat intelligence. When security stalwarts like Centrify and Palo Alto Networks combine...
Facebook, GDPR and the Right to Privacy: Three’s a Crowd?
Back in 2016 the European Union voted to pass the mother of all security laws, aimed at further extending the rights of its citizens to control how their data is used. The General Data Protection Regulation (GDPR) guards users against having their information shared without their explicit consent, and gives them the right to revoke that consent at any...
Roaming Mantis dabbles in mining and phishing multilingually
In April 2018, Kaspersky Lab published a blogpost titled ‘Roaming Mantis uses DNS hijacking to infect Android smartphones’. Roaming Mantis uses Android malware which is designed to spread via DNS hijacking and targets Android devices. This activity is located mostly in Asia (South Korea, Bangladesh and Japan) based on our telemetry data. Potential victims were redirected by DNS hijacking...
Analyst Insights – Building An Efficient Data Security Program with Forrester
Analyst Insights – Building An Efficient Data Security Program
This webinar was recorded on May 17, 2018.
- Read more
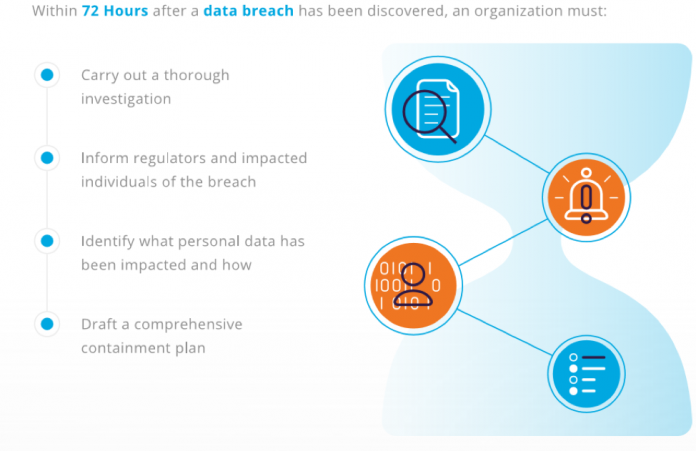
72 Hours: Understanding the GDPR Data Breach Reporting Timeline
We’re down to the wire with respect to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018.
Organizations that fail to comply could face fines of up to €20M (roughly $22M) or 4 percent of their annual global turnover from the prior year and we’ll soon see just how EU regulators will enforce the GDPR regulations.
One of...