North Korea’s APT37 Expands Toolkit to Breach Air-Gapped Networks
The security researchers from Zscaler ThreatLabz have also discovered five new tools deployed by the North Korean hacking group - Read more
Millions at Risk as Android Mental Health Apps Expose Sensitive Data
Oversecured flagged 1,575 flaws in 10 Android health apps with 14.7M installs, putting chats, CBT notes, and mood logs at risk, per BleepingComputer.
The post Millions at Risk as Android Mental Health Apps Expose Sensitive Data appeared first on TechRepublic. - Read more
UK Vulnerability Monitoring Service Cuts Unresolved Security Flaws by 75%
The UK government says its new Vulnerability Monitoring Service has cut unresolved security flaws by 75% and reduced cyber-attack fix times from nearly two months to just over a week - Read more
Europe’s ManoMano Hit: 38M Customer Records Compromised in Vendor Breach
ManoMano is notifying 38 million customers after a third-party customer service breach exposed personal data, highlighting growing supply chain security risks.
The post Europe’s ManoMano Hit: 38M Customer Records Compromised in Vendor Breach appeared first on TechRepublic. - Read more
Hook, line, and vault: A technical deep dive into the 1Phish kit
We analyze the evolution of the 1Phish phishing kit from a basic credential harvester into an MFA-aware, multi-stage phishing kit targeting 1Password users. - Read more
Odido – 1,520,769 breached accounts
In February 2026, Dutch telco Odido was the victim of a data breach and subsequent extortion attempt. Shortly after, 1M records containing 317k unique email addresses were published, followed by further releases exposing an additional 371k and then 833k unique email addresses, with the latter also including passport, driver’s licence and European national ID numbers. The exposed data includes...
Odido – 688,102 breached accounts
In February 2026, Dutch telco Odido was the victim of a data breach and subsequent extortion attempt. Following the incident, 1M records containing 317k unique email addresses were published, with the attackers threatening to leak additional data in the following days. That threat was subsequently carried out, with a further 1M records containing an additional 371k unique email addresses...
AWS successfully completed its first surveillance audit for ISO 42001:2023 with no findings
In November 2024, Amazon Web Services (AWS) was the first major cloud service provider to announce the ISO/IEC 42001 accredited certification for AI services, covering: Amazon Bedrock, Amazon Q Business, Amazon Textract, and Amazon Transcribe. In November 2025, AWS successfully completed its first surveillance audit for ISO 42001:2023, Artificial Intelligence Management System with no findings. This demonstrates...
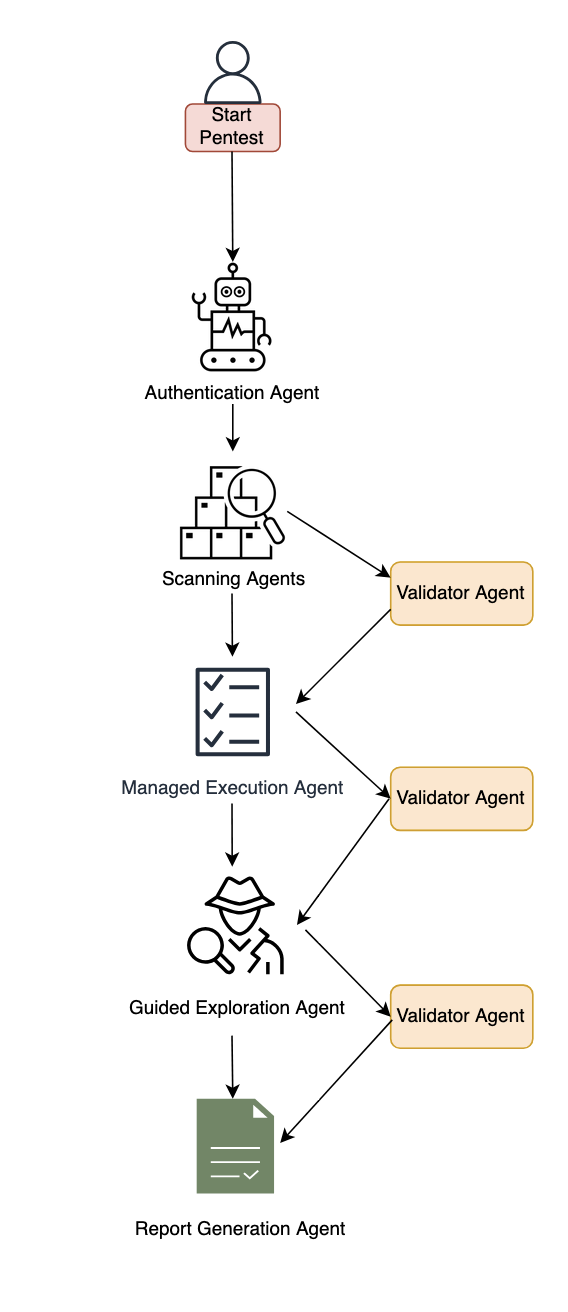
Inside AWS Security Agent: A multi-agent architecture for automated penetration testing
AI agents have traditionally faced three core limitations: they can’t retain learned information or operate autonomously beyond short periods, and they require constant supervision. AWS addresses these limitations with frontier agents—a new category of AI that performs complex reasoning, multi-step planning, and autonomous execution for hours or days. Multi-agent collaboration has emerged as a powerful approach that...
Henry IV, Hotspur, Hal, and hallucinations
Welcome to this week’s edition of the Threat Source newsletter. "'Tis dangerous to take a cold, to sleep, to drink; but I tell you, my lord fool, out of this nettle, danger, we pluck this flower, safety." - Hotspur, Shakespeare’s Henry IV, Part 1: Act 2 Scene 3 I get it. Hotspur is the quintessential hothead, and we all understand his place in the story. He’s famous for his fiery temperament...