Threats to macOS users
Introduction
The belief that there are no threats for the macOS operating system (or at least no serious threats) has been bandied about for decades. The owners of MacBooks and iMacs are only rivaled by Linux users in terms of the level of confidence in their own security, and we must admit that they are right to a certain degree:...
This is what our summer’s like
For the second summer straight, we cover the children’s interests during the period when they have enough leisure to give themselves full time to their hobbies. Modern children are active users of the internet, so most of their interests find reflection in their online activities, which are the subject of our today’s review.
Statistics collection principles
Kaspersky products scan the content...
Fully equipped Spying Android RAT from Brazil: BRATA
“BRATA” is a new Android remote access tool malware family. We used this code name based on its description – “Brazilian RAT Android”. It exclusively targets victims in Brazil: however, theoretically it could also be used to attack any other Android user if the cybercriminals behind it want to. It has been widespread since January 2019, primarily hosted in...
Incident Response report 2018
Download full report (PDF)
Introduction
This report covers our team’s incident response practices for the year 2018. We have thoroughly analyzed all the service requests, customer conversations and incident response deliverables to provide you an overview in numbers. The report includes statistics on how companies reveal data breaches and compromises, the attack vectors most commonly used by adversaries, how long they...
Spam and phishing in Q2 2019
Quarterly highlights
Spam through Google services
In the second quarter of 2019, scammers were making active use of cloud-based data storage services such as Google Drive and Google Storage to hide their illegal content. The reasoning behind this is simple: a link from a legitimate domain is seen as more trustworthy by both users and spam filters. Most often, such links...
Modern Skills for Modern CISOs
Modern Skills for Modern CISOs #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff;...
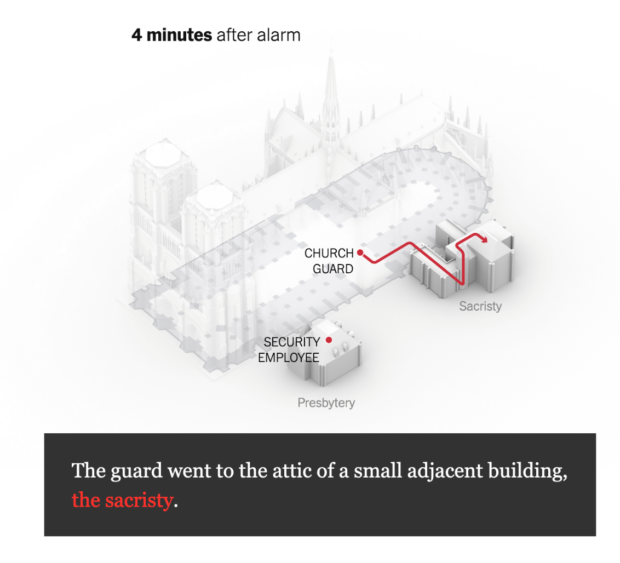
On Systems, Smoke Alerts, and Lessons Learned from The Paris Notre-Dame Cathedral Fire
There is a great exposé in the New York Times breaking down the timeline and mis-steps in response to the fire that occurred in the Notre-Dame Cathedral in Paris in April, 2019. Reading through the article, what I kept thinking about were the interesting parallels between fire response and cyber threat response.
What stood out to me immediately in the...
Imperva Security Update
I want to share details about a security incident at Imperva that resulted in a data exposure impacting our Cloud Web Application Firewall (WAF) product, formerly known as Incapsula. In this situation, we will do our best to honor the following principles:
To do the right thing for all of our constituents
To be fact and data driven – and to...
GUEST BLOG: A Gen Z’s Perspective on Cybersecurity
I had the pleasure to mentor a summer intern named Min Ji Kim, who is returning to NYU to continue her education next week. Before she left, Min Ji wrote a wonderful guest blog about what she learned about cybersecurity during her short time at Centrify. Enjoy!
A Gen Z’s Perspective on Cybersecurity
by Min Ji Kim
I was attracted to Centrify...