USB threats from malware to miners
Introduction
In 2016, researchers from the University of Illinois left 297 unlabelled USB flash drives around the university campus to see what would happen. 98% of the dropped drives were picked up by staff and students, and at least half were plugged into a computer in order to view the content. For a hacker trying to infect a computer network,...
Imperva Joins Global Cybersecurity Tech Accord
Imperva is dedicated to the global fight to keep people’s data and applications safe from cybercriminals. What this means for our Imperva Threat Research team is that we spend a lot of time researching new cyber attacks, creating mitigations and writing powerful software. We believe that nothing grows in a vacuum, and as such understand the importance of collaboration...
Threats posed by using RATs in ICS
While conducting audits, penetration tests and incident investigations, we have often come across legitimate remote administration tools (RAT) for PCs installed on operational technology (OT) networks of industrial enterprises. In a number of incidents that we have investigated, threat actors had used RATs to attack industrial organizations. In some cases, the attackers had stealthily installed RATs on victim organizations’...
Stay Secure with Day-One Support for iOS 12 and macOS Mojave
It’s that time of year again: time for all the latest and greatest from our friends in Apple Park (or the Apple Spaceship as locals call it). This week, Apple released iOS 12 and next week Apple will release the latest update for macOS, 10.14 Mojave.
We here at Centrify are excited for the new capabilities, the new look of...
Microsoft and Imperva Collaboration Bolsters Data Compliance and Security Capabilities
This article explains how Imperva SecureSphere V13.2 has leveraged the latest Microsoft EventHub enhancements to help customers maintain compliance and security controls as regulated or sensitive data is migrated to Azure SQL database instances.
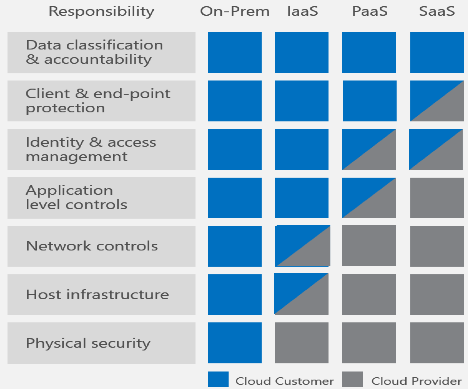
Database as a Service Benefits
Platform as a Service (PaaS) database offerings such as Azure SQL are rapidly becoming a popular option for organizations deploying databases in the...
Integrating Security into DevOps Without Losing Momentum
Integrating Security into DevOps Without Losing Momentum #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; }...
New trends in the world of IoT threats
Cybercriminals’ interest in IoT devices continues to grow: in H1 2018 we picked up three times as many malware samples attacking smart devices as in the whole of 2017. And in 2017 there were ten times more than in 2016. That doesn’t bode well for the years ahead.
We decided to study what attack vectors are deployed by cybercriminals to...
Explainer Series: RDaaS Security and Managing Compliance Through Database Audit and Monitoring Controls
As organizations move to cloud database platforms they shouldn’t forget that data security and compliance requirements remain an obligation. This article explains how you can apply database audit and monitoring controls using Imperva SecureSphere V13.2 when migrating to database as a service cloud offering.
Introduction to RDaaS
A Relational Database as a Service (RDaaS) provides the equipment, software, and infrastructure needed...