Forrester Names Centrify a Leader in Privileged Identity Management
Today Forrester Research released The Forrester Wave: Privileged Identity Management, Q4 20181. Evaluating 11 vendors, Forrester named Centrify a Leader.
Here at Centrify, we believe this is a strong validation of Centrify’s Zero Trust Privilege approach to privileged identity management. A complimentary version of this report is available for download here.
Centrify is redefining the legacy approach to Privileged Identity Management by delivering cloud-ready Zero...
A new exploit for zero-day vulnerability CVE-2018-8589
Yesterday, Microsoft published its security bulletin, which patches a vulnerability discovered by our technologies. We reported it to Microsoft on October 17, 2018. The company confirmed the vulnerability and assigned it CVE-2018-8589.
In October 2018, our Automatic Exploit Prevention (AEP) systems detected an attempt to exploit a vulnerability in Microsoft’s Windows operating system. Further analysis revealed a zero-day vulnerability in...
Five Tips for NERC CIP Audits
Five Tips for NERC CIP Audits #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
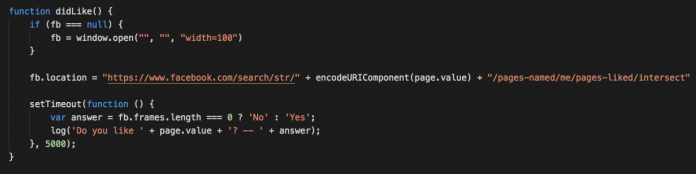
Patched Facebook Vulnerability Could Have Exposed Private Information About You and Your Friends
In a previous blog we highlighted a vulnerability in Chrome that allowed bad actors to steal Facebook users’ personal information; and, while digging around for bugs, thought it prudent to see if there were any more loopholes that bad actors might be able to exploit.
What popped up was a bug that could have allowed other websites to extract private...
New Docker-based Dev Pipeline: Microservice Projects Just Got A ‘Speed-Boost’
A bulwark of software engineering projects, the development pipeline is an automated process used to deliver changes from development through to production; enabling near real-time updates.
The dev pipeline is a critical time saver as it enables you to:
Avoid mistakes (and wasted time as a result) through automation.
Supply quick feedback for any changes in the software (good or bad).
Operate...
The Base of Cyber-Attacks: Credential Harvesting
Cyber attackers long ago figured out that the easiest way to gain access to sensitive data is by compromising an end user’s identity and credentials. According to the Verizon 2017 Data Breach Investigation Report, 81% of hacking-related breaches leverage either stolen, default, or weak credentials. Often these credentials belong to privileged users, providing cyber adversaries the “keys to the...
The Dos and Don’ts of DevOps
The Dos and Don'ts of DevOps #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
Spam and phishing in Q3 2018
Quarterly highlights
Personal data in spam
We have often said that personal data is candy on a stick to fraudsters and must be kept safe (that is, not given out on dubious websites). It can be used to gain access to accounts and in targeted attacks and ransomware campaigns.
In Q3, we registered a surge of fraudulent emails in spam traffic. This...