CEO Fraud Continues to Rear Its Ugly Head
As CEO of Centrify, I have been writing about “CEO Fraud” — whereby scammers send emails that impersonate senior executives to obtain money or data — for well over three years now.
I have blogged about it based on first-hand encounters, presented on it and the broader topic of “business email compromise” (BEC) at the 2016 RSA Conference, and was...
The Year Ahead: Cybersecurity Trends To Look Out for In 2019
A Proven Record Tracking Cybersecurity Trends
This time of the year is always exciting for us, as we get to take a step back, analyze how we did throughout the year, and look ahead at what the coming year will bring. Taking full advantage of our team’s expertise in data and application security, and mining insights from our global customer...
Remotely controlled EV home chargers – the threats and vulnerabilities
We are now seeing signs of a possible shift in the field of personal transport. Recent events such as the ‘dieselgate’ scandal undermine customer and government confidence in combustion engines and their environmental safety. At the same time there has been a big step forward in the development of electric vehicles. In addition to favorable media coverage, modern EVs...
Read: New Attack Analytics Dashboard Streamlines Security Investigations
Attack Analytics, launched this May, aimed to crush the maddening pace of alerts that security teams were receiving. For security analysts unable to triage this avalanche of alerts, Attack Analytics condenses thousands upon thousands of alerts into a handful of relevant, investigable incidents. Powered by artificial intelligence, Attack Analytics is able to automate what would take a team of...
Zero Trust Lessons from a Holiday Classic
Every year when the holidays roll around, I’m amazed at the way shopping deals dominate the headlines. Black Friday and Cyber Monday are annual juggernauts that produce some amazing opportunities for shoppers and retailers alike.
Yet this year, even the mighty shopping season has taken back-seat to the continuing domination of security breaches in the press. With $114 billion being...
Zero-day in Windows Kernel Transaction Manager (CVE-2018-8611)
Executive summary
In October 2018, our AEP (Automatic Exploit Prevention) systems detected an attempt to exploit a vulnerability in the Microsoft Windows operating system. Further analysis led us to uncover a zero-day vulnerability in ntoskrnl.exe. We reported it to Microsoft on October 29, 2018. The company confirmed the vulnerability and assigned it CVE-2018-8611. Microsoft just released a patch, part of...
PCI DSS and the CIS Controls
PCI DSS and the CIS Controls #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
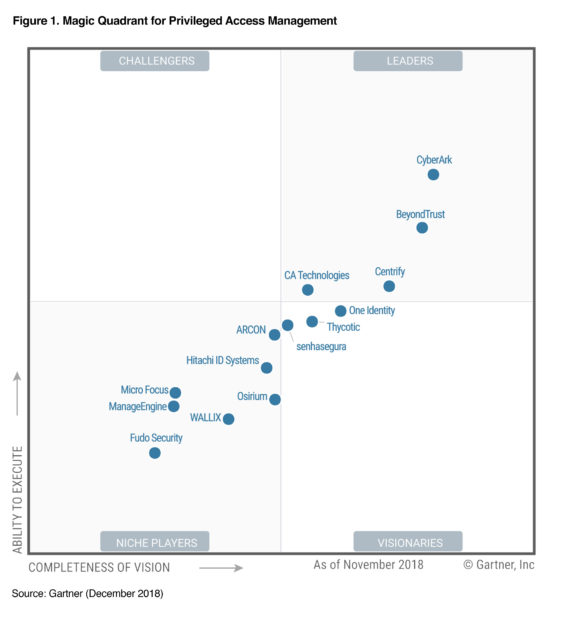
Gartner Names Centrify a Leader in Magic Quadrant for Privileged Access Management (PAM)
On December 3, 2018 Gartner released The Magic Quadrant for Privileged Access Management, Q4 2018. Evaluating 14 vendors, Gartner positioned Centrify in the LEADERS quadrant.
Here at Centrify, we believe this is a strong validation of Centrify’s Zero Trust Privilege approach to privileged access management. A complimentary version of this report is available for download here.
As breaches and attacks grow, the market is...
DarkVishnya: Banks attacked through direct connection to local network
While novice attackers, imitating the protagonists of the U.S. drama Mr. Robot, leave USB flash drives lying around parking lots in the hope that an employee from the target company picks one up and plugs it in at the workplace, more experienced cybercriminals prefer not to rely on chance. In 2017-2018, Kaspersky Lab specialists were invited to research a...



![[eBook] Building A Cyber-Secure Culture](http://www.dataproof.co.za/wp-content/uploads/2018/12/ebook-building-a-cyber-secure-culture.png)