Hundreds of Vulnerable Docker Hosts Exploited by Cryptocurrency Miners
Docker is a technology that allows you to perform operating system level virtualization. An incredible number of companies and production hosts are running Docker to develop, deploy and run applications inside containers.
You can interact with Docker via the terminal and also via remote API. The Docker remote API is a great way to control your remote Docker host,...
Centrify RSA Booth 6445: Where Zero Trust Privilege Partners Take the Stage
If there was one clear takeaway from the 2018 RSA Conference, it was that Zero Trust was ready to take off.
It seemed like everywhere you turned, Zero Trust was staring you in the face. Oh wait, that was just the Centrify marketing blitz that overtook San Francisco and Moscone Center last April!
ZERO TRUST, 10 MONTHS LATER
Fast-forward 10 months ahead...
Don’t Let Security Needs Halt Your Digital Transformation. Imperva FlexProtect Offers Agile Security for any Enterprise.
Is your enterprise in the midst of a digital transformation? Of course it is. Doing business in today’s global marketplace is more competitive than ever. Automating your business processes and infusing them with always-on, real-time applications and other cutting-edge technology is key to keeping your customers happy, attracting and retaining good workers, transacting with your partners, and growing your...
Start Your Engines! It’s Zero Trust Privilege Test Drive Season!
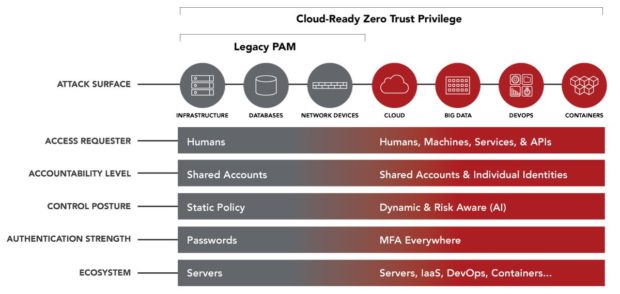
As organizations struggle to protect the ever-expanding attack surface, they not only have to secure access to infrastructure, databases, and network devices, but also extend security controls to cloud environments.
The modern threatscape now includes Big Data projects, DevSecOps, and hundreds of containers or microservices that represent what used to be a single server.
At Centrify, we believe that legacy PAM...
NEW CENTRIFY SURVEY: Too Much Privilege, Not Enough PAM Powered by Zero Trust
I’m both a technology guy, and a numbers guy.
I have Bachelor of Science degrees in both Accounting and Computer Science. I’ve held the CFO and VP of Finance titles at technology companies throughout my career, including at Centrify where I was CFO for 7 years before becoming CEO in January.
But I’ve never painted myself as only a numbers guy...
How to Attack and Defend a Prosthetic Arm
The IoT world has long since grown beyond the now-ubiquitous smartwatches, smartphones, smart coffee machines, cars capable of sending tweets and Facebook posts and other stuff like fridges that send spam. Today’s IoT world now boasts state-of-the-art solutions that quite literally help people. Take, for example, the biomechanical prosthetic arm made by Motorica Inc. This device helps people who...
Latest Drupal RCE Flaw Used by Cryptocurrency Miners and Other Attackers
Another remote code execution vulnerability has been revealed in Drupal, the popular open-source Web content management system. One exploit — still working at time of this writing — has been used in dozens of unsuccessful attacks against our customers, with an unknown number of attacks, some likely successful, against other websites.
Published on February 20th, the new vulnerability (known...
No One is Safe: the Five Most Popular Social Engineering Attacks Against Your Company’s Wi-Fi Network
Your Wi-Fi routers and access points all have strong WPA2 passwords, unique SSIDs, the latest firmware updates, and even MAC address filtering. Good job, networking and cybersecurity teams! However, is your network truly protected? TL;DR: NO!
In this post, I’ll cover the most common social engineering Wi-Fi association techniques that target your employees and other network users. Some of them...
Gartner Names PAM a Top Security Project (AGAIN!) in 2019
Last June at the 2018 Gartner Security & Risk Management Summit, the analyst firm issued a “Smarter with Gartner” paper outlining the Top 10 security projects for 2018, which included Privileged Account Management. While Gartner clarified that the ten projects were in no particular order, PAM was right there at the top.
This was not a surprise to Centrify, as...