I’m both a technology guy, and a numbers guy.
I have Bachelor of Science degrees in both Accounting and Computer Science. I’ve held the CFO and VP of Finance titles at technology companies throughout my career, including at Centrify where I was CFO for 7 years before becoming CEO in January.
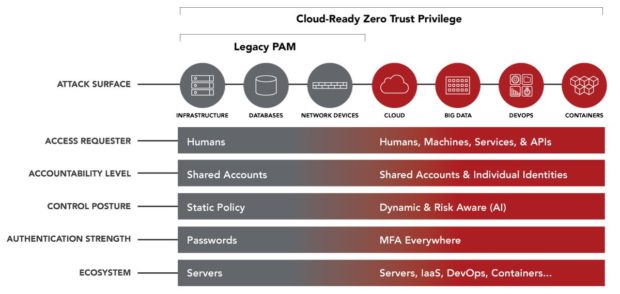
But I’ve never painted myself as only a numbers guy because I’ve always had a very keen eye on the technology and operations. As CEO, now more than ever, I’m laser-focused on our innovation and ability to execute on our vision, which is to redefine legacy PAM with cloud-ready Zero Trust Privilege to stop the leading cause of breaches: privileged credential abuse.
That vision is powered by three core components:
- Our approach of Privileged Access Management powered by Zero Trust, which goes beyond legacy PAM to secure modern attack surfaces.

- Centrify Zero Trust Privilege Services, a cloud-ready solution that verifies who is requesting access, provides the context of the request, and the risk of the access environment to help customers grant least privilege access.

- A 3-pronged implementation methodology to help our customers reduce risk and strengthen their security postures on their journey to Zero Trust Privilege maturity.

But, I still love numbers, and as a technology executive who loves numbers, I was thrilled to see the results of a survey we conducted recently with FINN Partners, polling 1,000 IT decision makers (500 U.S./500 U.K.) about their awareness of the privileged credential threats their facing, their understanding of the PAM market, and how Zero Trust can help reduce their risk of becoming the next data breach headline.
CONFIRMED: PRIVILEGE IS LEADING ATTACK VECTOR
One of the biggest takeaways from the survey:

Let me tell you why this is big.
First, it confirms what we already know: the majority of cyber-attacks abuse privileged credentials, making it the leading attack vector.
We’ve said or written it a thousand times: attackers no longer “hack” in, they log in using weak credentials and then fan out, seeking privileged access to critical infrastructure and sensitive data.
Second, up until now, we’ve relied on a Forrester estimate that 80% of data breaches involve privileged credentials. Now we have empirical data that supports that estimate. Three out of 4 breaches abuse privileged access.
That’s why Gartner named PAM a Top 10 Security Project (AGAIN!) in 2019.
STILL NOT PRIORITIZING PAM
What’s concerning about the survey, however, is that despite knowing privilege is involved in the majority of breaches, most organizations and IT leaders are not prioritizing PAM or implementing it effectively. What’s worse, they continue to grant too much trust and too much privilege.
There are some very basic PAM capabilities and best practices that are still not being implemented, namely:
- 52% of respondents do not have a password vault! This is PAM 101, and one the very first steps of the PAM maturity model. Over half aren’t even vaulting privileged passwords, which means they’re probably written down on shared spreadsheets.

- 63% indicate their companies usually take more than one day to shut off privileged access for employees who leave the company. In an age when insiders are just as much a threat as outsiders, this is unacceptable. Privileged access needs to be revocable instantly.
- 21% still have not implemented Multi-Factor Authentication (MFA) for privileged administrative access. While it’s encouraging that 4 out of 5 are using MFA, there should be 100% MFA to effectively enforce Zero Trust.
Two more stats that caught my eye (and should catch yours too):
- 35% were not positive what PAM is. If this was a survey of average consumers, that wouldn’t surprise me. But these are IT decision makers! They should know what PAM is!
- 65% are still sharing root or privileged access to systems and data at least somewhat often. Identity consolidation is the second leg of the stool of risk reduction with regards to PAM best practices. Organizations need to get here quickly to decrease the overall number of accounts and passwords, and, ultimately, reduce the attack surface.

THE MODERN THREATSCAPE IS NOT SECURE
If organizations are still struggling to implement some of the most basic or required PAM strategies, then it’s not surprising that the survey revealed most are also not securing modern attack surfaces.

Legacy PAM solutions simply cannot secure modern attack surfaces. Organizations need to quickly move to Zero Trust Privilege backed by cloud-ready services that minimize the attack surface, improve audit and compliance visibility, and reduce risk, complexity and costs for the modern, hybrid enterprise.
Download the survey report now: http://bit.ly/CentrifySurvey
The post NEW CENTRIFY SURVEY: Too Much Privilege, Not Enough PAM Powered by Zero Trust appeared first on Secure Thinking by Centrify.