Cybersecurity Skills Gap Survey 2019
Cybersecurity Skills Gap Survey 2019 #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{ background-color:#ffffff;...
Spam and phishing in 2018
Numbers of the year
The share of spam in mail traffic was 52.48%, which is 4.15 p.p. less than in 2017.
The biggest source of spam this year was China (11.69%).
74.15% of spam emails were less than 2 KB in size.
Malicious spam was detected most commonly with the Win32.CVE-2017-11882 verdict.
The Anti-Phishing system was triggered 482,465,211 times.
18.32% of unique users encountered phishing.
Global...
A predatory tale: Who’s afraid of the thief?
In mid-February, Kaspersky Lab received a request for incident response from one of its clients. The individual who initially reported the issue to our client refused to disclose the origin of the indicator that they shared. What we do know is that it was a screenshot from one of the client’s internal computers taken on February 11 while an...
Mapping Communication Between Facebook Accounts Using a Browser-Based Side Channel Attack
A now-patched vulnerability in the web version of Facebook Messenger allowed any website to expose who you have been messaging with.
In a previous post, I showed how your Facebook likes, location history, and other metadata could have been extracted from your Facebook account using a side-channel attack I named “Cross-Site Frame Leakage,” or CSFL for short.
In this post, I’ll...
Financial Cyberthreats in 2018
Introduction and Key Findings
The world of finance has been a great source of income cybercriminals across the world due to an obvious reason – money. While governments and organizations have been investing in new methods to protect financial services, malicious users have been investing in how to bypass them. This has fueled many changes in how online financial services...
Time to Retire “The Year Of…” at RSA 2019
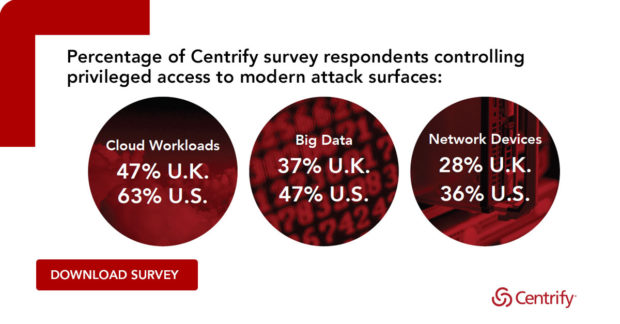
Today at the RSA Security Conference, we announced Centrify’s Cloud-Ready Zero Trust Privilege Services architecture, including a wide range of enhancements that redefine legacy Privileged Access Management (PAM). If you are at the show, we hope you pay us a visit in Booth 6445 where we can demo a range of DevOps, Automation, hybrid cloud, and infrastructure security protections...
Case Study: Keeping the Lights On with NERC CIP Compliance from Tripwire
Case Study: Keeping the Lights On with NERC CIP Compliance from Tripwire #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important;...






![[Case Study] Preventing Information Security Silos](http://www.dataproof.co.za/wp-content/uploads/2019/03/case-study-preventing-information-security-silos.jpg)