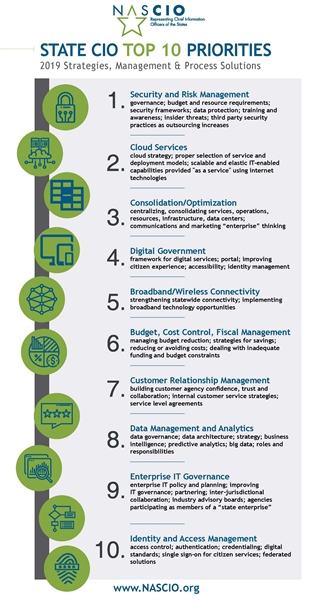
NASCIO CIO Top Priorities in a Zero Trust World
Many state CIOs are struggling to manage the onslaught of priorities that are captured in the NASCIO Top 10 Policy and Technology Priorities for 2019, ranging from enabling cloud services to the digital government to IT governance. While their mission mandates tackling these priorities, they cannot solely focus on their implementation, but must also bolster cyber security and abide...
Building a Mature Vulnerability Management Program
Building a Mature Vulnerability Management Program #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100% !important; } body,#backgroundTable{...
APT trends report Q1 2019
For just under two years, the Global Research and Analysis Team (GReAT) at Kaspersky Lab has been publishing quarterly summaries of advanced persistent threat (APT) activity. The summaries are based on our threat intelligence research and provide a representative snapshot of what we have published and discussed in greater detail in our private APT reports. They aim to highlight...
I know what you did last summer, MuddyWater blending in the crowd
Introduction
MuddyWater is an APT with a focus on governmental and telco targets in the Middle East (Iraq, Saudi Arabia, Bahrain, Jordan, Turkey and Lebanon) and also a few other countries in nearby regions (Azerbaijan, Pakistan and Afghanistan).
MuddyWater first surfaced in 2017 and has been active continuously, targeting a large number of organizations. First stage infections and graphical decoys have...
Centrify Achieves FedRAMP Authorization
Centrify received exciting news this week that we are now FedRAMP Authorized!
For those who don’t know about FedRAMP, it is a government-wide program that provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.
FedRAMP Authorization is an important qualification that significantly smooths the process of selling cloud technology solutions to government agencies. We...
Developers Versus Automation Engineers: How We Ended the Fighting with the Right CI Process
Hey developers and DevOps professionals: what if I told you that how you wrap and execute your automation tests could be the key to making your development process faster, more professional and stable, and stop the bickering between your developers and automation teams?
This post will describe how we, the Automation team, created a new Continuous Integration (CI) process...
Maintaining Privacy in the Cloud [Podcast Discussion]
Not long ago I joined Brian Contos, CISO and VP of Product Innovation at Verodin, for one of his Verodin Cybersecurity Effectiveness Podcasts.
It’s been about 10 years since I worked with Brian at Imperva when he was the Chief Security Strategist. Back then, he was the one traveling the world, meeting with organizations who were dealing with some of...
Better Together: Fix Vulnerabilities Faster with FIM and VM
Better Together: Fix Vulnerabilities Faster with FIM and VM #outlook a{ padding:0; } body{ width:100% !important; } .ReadMsgBody{ width:100%; } .ExternalClass{ width:100%; } body{ -webkit-text-size-adjust:none; } body{ margin:0; padding:0; } img{ border:0; height:auto; line-height:100%; outline:none; text-decoration:none; } table td{ border-collapse:collapse; } #backgroundTable{ height:100% !important; margin:0; padding:0; width:100%...