Fortnite Scammers Approaching $1m in Annual Takings
When something seems too good to be true, it probably is. It’s a hard lesson to learn and, in this case, one that’s being...
The Data Breach ‘Kill Chain’: Early Detection is Key
Today, organizations rely heavily on data, with a big portion of that data made up of sensitive information. As organizations become the custodians of...
Imperva Cloud Security Now Available Through UK Government’s GCloud 10 Digital Marketplace
Building on the success of Imperva listing our market-leading, single stack Incapsula cloud platform for DDOS protection; CDN; load balancing and WAF on the...
Need for Speed: Optimizing Data Masking Performance and Providing Secure Data for DevOps Users
Let’s start with a pretty common life experience — you identify a need (e.g., transportation), you evaluate your options (e.g., evaluate car manufacturers, various...
Building an Effective API Security Strategy: Easy If You Have the Right Tools
In their approach to application programming interface (API) security, organizations exposing web APIs must balance ease of access with control. Like the bank robber...
Cloud Security For The Healthcare Industry: A No-Brainer
The healthcare industry has become one of the likeliest to suffer cyber-attacks, and there’s little wonder why. Having the financial and personal information of scores...
Back to Basics: Let’s Forget About the GDPR… For A Moment
At this point it’s fairly safe to assume that most everyone in the business of “data” has heard of the European Union (EU)-wide General...
Cloud Migration Fundamentals: Overcoming Barriers to App Security [Infographic]
As more organizations move to the cloud, the line of responsibility in securing applications can become rather blurred.
The concept of control has historically rested...
How To Leverage Data Access Analytics for Effective Breach Detection
Detecting and preventing data breaches is a challenge for most, if not all, enterprises. In fact, according to a study released in 2017, 78%...
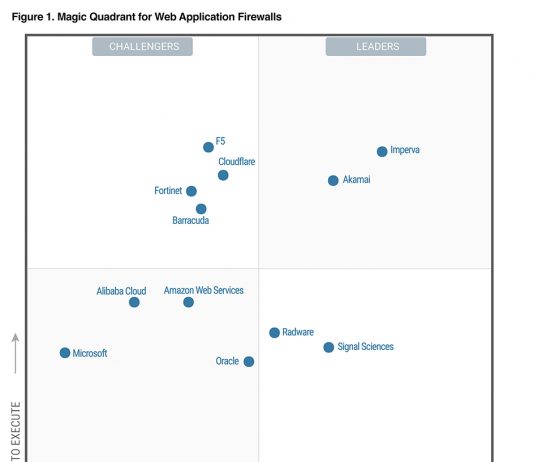
The Gartner CISO Playbook: Leveraging Effective Control in the Cloud
For as long as we can remember, the concept of control has rested comfortably in physical location and ownership. It’s simple, if you could...



![Cloud Migration Fundamentals: Overcoming Barriers to App Security [Infographic]](http://www.dataproof.co.za/wp-content/uploads/2018/07/cloud-migration-fundamentals-overcoming-barriers-to-app-security-infographic-218x150.png)









