Integrate Your Ticketing System into Database Security to Prevent DBA Privilege Abuse
Many of the recent high-profile data security breaches were made by trusted insiders. They are often database administrators (DBAs) who are highly privileged and...
A Deep Dive into Database Attacks [Part I]: SQL Obfuscation
Today, data breaches are a threat to every organization. According to a report from Risk Based Security covering the first half of 2017, over 6...
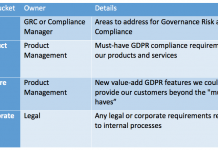
One GRC Manager’s Practical Approach to GDPR Readiness
With about four months to go before the GDPR becomes effective many companies are still struggling with where to start. You’re not alone. According...
2017 OWASP Top 10: The Good, the Bad and the Ugly
Since its founding in 2001, the Open Web Application Security Project (OWASP) has become a leading resource for online security best practices. In particular,...
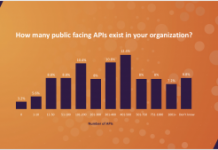
Survey: APIs a Growing Cybersecurity Risk
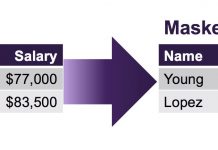
Like a lot of people, your mobile phone number is probably easily accessible to anyone with a bit of searching. Imagine if someone could...
Improve the ROI of Your Database Protection Investment
When an organization considers switching a mission-critical compliance or security system from one vendor’s solution to another it’s a very big decision. There is...
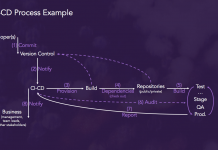
Security Strategies for DevOps, APIs, Containers and Microservices
More and more IT professionals see DevSecOps, a practice which integrates security measures earlier in the development process to improve production code quality, as...
Cloud Database Migration Peer Insights [Report]
Not long ago, for security, compliance or other reasons, it was unthinkable for many regulated organizations to move sensitive data into the cloud. It’s...
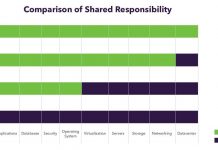
Cloud Migration Fundamentals
The advantages offered by a cloud-based environment make it an easy decision for most companies to make. Still, there are numerous critical choices to...
Three Reasons Why GDPR Encourages Pseudonymization
The General Data Protection Regulation (GDPR) is the European Union’s new data regulation designed to provide individuals with rights and protections over their personal...



![A Deep Dive into Database Attacks [Part I]: SQL Obfuscation](http://www.dataproof.co.za/wp-content/uploads/2018/02/a-deep-dive-into-database-attacks-part-i-sql-obfuscation-218x150.png)


![Cloud Database Migration Peer Insights [Report]](http://www.dataproof.co.za/wp-content/uploads/2018/01/cloud-database-migration-peer-insights-report-218x150.png)