Monitoring Data & Data Access to Support Ongoing GDPR Compliance – Part III: Tools
The new European Union (EU)-wide General Data Protection Regulation (GDPR) was signed into law in late April 2016, and the compliance deadline came into...
Clustering App Attacks with Machine Learning (Part 2): Calculating Distance
In our previous post in this series we discussed our motivation to cluster attacks on apps, the data we used and how we enriched...
Clustering App Attacks with Machine Learning Part 1: A Walk Outside the Lab
A lot of research has been done on clustering attacks of different types using machine learning algorithms with high rates of success. Much of...
Zero to Account Takeover: How I ‘Impersonated’ Someone Else Using Auth0
There’s a fine line between an unintended use and a bug; this was my conclusion after taking a look at Auth0, an identity-as-a-service offering...
New research shows 75% of ‘open’ Redis servers infected
Since our initial report on the RedisWannaMine attack that propagates through open Redis and Windows servers, we’ve been hearing about more and more attacks...
Five Ways Imperva Attack Analytics Helps You Cut Through the Event Noise
The maddening volume of events security teams have to deal with each day is growing at an exponential pace, making it increasingly difficult to effectively...
See If You’re GDPR-Ready With Our Last-Minute Checklist
Time’s just about run out to get all your ducks in a row for the EU’s General Data Protection Regulation (GDPR) going into effect...
Facebook, GDPR and the Right to Privacy: Three’s a Crowd?
Back in 2016 the European Union voted to pass the mother of all security laws, aimed at further extending the rights of its citizens...
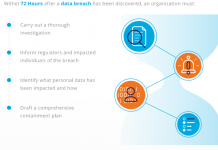
72 Hours: Understanding the GDPR Data Breach Reporting Timeline
We’re down to the wire with respect to the General Data Protection Regulation (GDPR) compliance deadline of May 25, 2018.
Organizations that fail to comply...
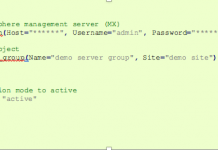
Imperva Python SDK – We’re All Consenting SecOps Here
Managing your WAF can be a complicated task. Custom policies, signatures, application profiles, gateway plugins… there’s a good reason ours is considered the best...