Want to See What A Live DDoS Attack Looks Like?
We’re fortunate enough to have had Andy Shoemaker, founder of NimbusDDoS, and our own Ofer Gayer chat about DDoS attacks and shed some light on...
Configuring Imperva SecureSphere for GDPR Compliance: Part One
Time is running out. 23 days until GDPR enforcement
The GDPR effective date is less than a month away and, given the significant risk and...
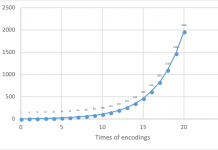
The Catch 22 of Base64: Attacker Dilemma from a Defender Point of View
Web application threats come in different shapes and sizes. These threats mostly stem from web application vulnerabilities, published daily by the vendors themselves or...
Drupalgeddon3: Third Critical Flaw Discovered
For the third time in the last 30 days, Drupal site owners are forced to patch their installations. As the Drupal team noted a...
Drupalgeddon 2.0: Are Hackers Slacking Off?
Ever since March 28th, when Drupal published a patch for a RCE named Drupalgeddon 2.0 (SA-CORE-2018-002/CVE-2018-7600), Imperva has been monitoring our cloud looking for...
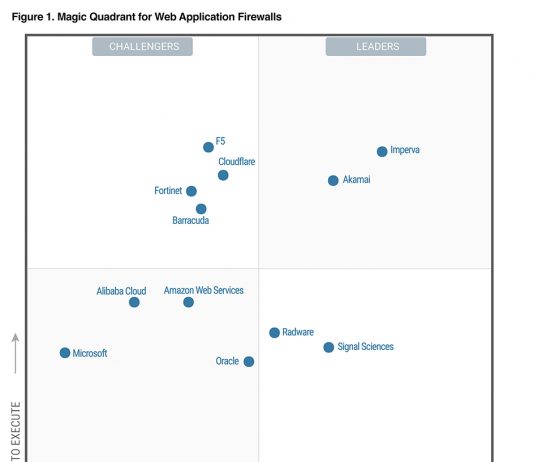
Securing Modern Web Applications: Threats and Types of Attacks
Web Application Firewalls are the most advanced firewall capabilities available to IT teams. Deploying the appropriate WAF is important, especially these days when the...
How to Tune Your Database Security to Protect Big Data
As digital information and data continues to accumulate worldwide, new big data solutions grow more and more popular. The introduction of IoT into our...
A Deep Dive into Database Attacks [Part IV]: Delivery and Execution of Malicious Executables...
In a previous post we covered different techniques for execution of SQL and OS commands through Microsoft SQL server that can be used for...
Streamline Compliance with SWIFT Customer Security Program Requirements
Transferring money from our bank accounts has never been easier than it is today. With a single click on our smartphones, we can transfer...
DevOps-Ready WAF: Scaling Security for a More Agile Environment
With the maturation of DevOps, the growing concern around the security and compliance of more agile application development systems has made 2018 the year...


![A Deep Dive into Database Attacks [Part IV]: Delivery and Execution of Malicious Executables through SQL Commands (MySQL)](http://www.dataproof.co.za/wp-content/uploads/2018/04/a-deep-dive-into-database-attacks-part-iv-delivery-and-execution-of-malicious-executables-through-sql-commands-mysql-218x150.png)









