Subscribe to Data Insider
Subscribe to <span style="color: #11111; font-style: bold; letter-spacing: -1px;">DATA</span><span style="color: #E51892; font-style: italic; font-style: bold; letter-spacing: -1px;">INSIDER</span>
.blog_subscribe_block{ margin-top: 50px !important; margin-left: auto;...
NEW: Vulnerability and Assessment Scanning for Your AWS Cloud Databases
Scuba is a free and easy-to-use tool that uncovers hidden security risks. Scuba is frequently updated with content from Imperva’s Defense Center researchers.
With Scuba...
Tax refund, or How to lose your remaining cash
Every year, vast numbers of people around the globe relish the delightful prospect of filling out tax returns, applying for tax refunds, etc. Given...
C-Suite Disconnect is Weakening Cybersecurity
Today, Centrify announced a new research study conducted with Dow Jones Customer Intelligence titled, “CEO Disconnect is Weakening Cybersecurity.” The report sheds light on...
New Research: Crypto-mining Drives Almost 90% of All Remote Code Execution Attacks
It’s early in 2018 and we have already witnessed one of the top contenders in this year’s web application attacks. Continuing the trend from...
A Slice of 2017 Sofacy Activity
Sofacy, also known as APT28, Fancy Bear, and Tsar Team, is a highly active and prolific APT. From their high volume 0day deployment to...
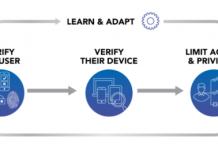
Break the Trust and Stop the Breach: The Zero Trust Security Model
As 2018 is upon us, it’s time to take stock of our new realities and commit to better behavior that benefits us and our...
Spam and phishing in 2017
Figures of the year
The share of spam in mail traffic came to 56.63%, down 1.68% against 2016.
The biggest source of spam remains the US...
Integrate Your Ticketing System into Database Security to Prevent DBA Privilege Abuse
Many of the recent high-profile data security breaches were made by trusted insiders. They are often database administrators (DBAs) who are highly privileged and...
Five Best Practices for Zero Trust Security
The Centrify Zero Trust Security model is effective because it allows organizations to remove trust from the equation entirely. Based on the assumption that...